Abuse
Company responsibility and compliance
I blogged a few times recently about Zoho and their issues with malicious actors abusing their platform. They asked me to post the following statement from their CEO Sridhar Vembu.
Read MoreCheck your abuse addresses
Even if you have excellent policies and an effective, empowered enforcement team you can still have technical problems that can cause you to drop abuse mail, and so lose the opportunity to get a bad actor off your network before they damage your reputation further.
Read MoreSubscription bombing and abuse prevention
A few weeks ago ProPublica was the victim of a subscription bomb attack. Julia Angwin found my blog post on the subject and contacted me to talk about the post. We spent an hour or so on the phone and I shared some of the information we had on the problem. Julie told me she was interested in investigating this further problem further. Today, ProPublica published Cheap Tricks: the Low Cost of Internet Harassment.
For those of us deeply involved in the issue, there isn’t too much that comes as a surprise in that article. But it’s a good introduction to folks who may not be aware of the existence of subscription bombing.
Julia does mention something I have been thinking about: abuse and anonymity online. Can we continue to have anonymous or pseudonymous identities on the Internet? Should we?
One of the challenges a lot of companies are struggling with is that anonymity can protect oppressors as well as their targets. How do we support “good” anonymity without enabling “bad” anonymity? I’ve always thought anonymity was an overall good and the fact that it’s abused sometimes didn’t mean it should be taken away. Banning anonymity online might seem to fix the problem of abuse, except it really doesn’t and it comes with its own set of problems.
Let’s be honest, these are hard questions and ones that do need to be addressed. A lot of the tools abuse and security desks currently have rely on volume of complaints. This can result in the targets getting shut down due to false complaints while the perpetrators keep their accounts open. It means subscription bombs can target a few individuals and occur undetected for months.
Big companies in Silicon Valley love to rely on their algorithms and machine learning and AI and code to automate things. But the automation only works after you create working processes. Throwing code at the problem doesn’t work unless you have a picture of the scope of the problem. And a reliance on code ends up with Facebook asking people to upload nudes of themselves to prevent nudes on Facebook. Likewise, throwing cheap labor at the problem isn’t a solution, either.
I don’t have the answers, I don’t think anyone does. But we need to think harder about these problems and address them sooner rather than later. The internet is too important to let abusers break it.
The Blighty Flag
Back in the dark ages (the late ’90s) most people used dialup to connect to the internet. Those people who had broadband could run all sorts of services off them, including websites and mail servers and such. We had a cable modem for a while handling mail for blighty.com.
At that time blighty.com had an actual website. This site hosted some of the very first online tools for fighting abuse and tracking spam. At the same time, both of us were fairly active on USENET and in other anti-spam fora. This meant there were more than a few spammers who went out of their way to make our lives difficult. Sometimes by filing false complaints, other times by actually causing problems through the website.
At one point, they managed to get a complaint to our cable provider and we were shut off. Steve contacted their postmaster, someone we knew and who knew us, who realized the complaint was bogus and got us turned back on. Postmaster also said he was flagging our account with “the blighty flag” that meant he had to review the account before it would be turned off in the future.
I keep imagining the blighty flag looking like this in somebody’s database.
That is to say, sometimes folks disable accounts they really shouldn’t be disabling. Say, for instance: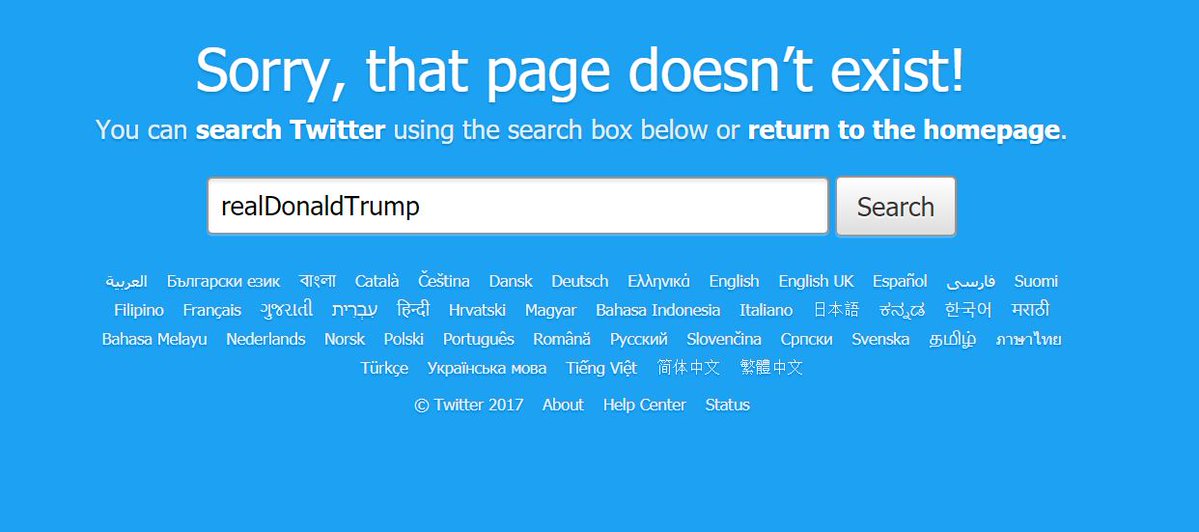
This was an accident by a twitter employee, according to a post by @TwitterGov
Responding to complaints
I sent in a complaint to an ESP earlier today. This was mail from a major UK retailer to an address that is not used to sign up for mail. It’s part of an ongoing stream of spam related to UK services and products. I believe most of this is because one of the data selling companies has that address associated with someone who is not me.
I did explain I believed this was a purchased address but I’m wondering if I will get a response. The address isn’t one of those I regularly use so there isn’t a connection between “Laura, deliverability person” and “Laura, spam victim.” There are some industry folks who go out of their way to respond to my complaints. That’s always rewarding.
On a more theoretical level, I can make good arguments for responding and good arguments for not responding.
September 2016: The month in email
Happy October, everyone. As we prepare to head to London for the Email Innovations Summit, we’re taking a look back at our busy September. As always, we welcome your feedback, questions, and amusing anecdotes. Seriously, we could use some amusing anecdotes. Or cat pictures.

We continued to discuss the ongoing abuse and the larger issues raised by attacks across the larger internet infrastructure. It’s important to note that even when these attacks aren’t specifically targeting email senders, security issues affect all of us. It’s important for email marketers to understand that increased attacks do affect how customers view the email channel, and senders must take extra care to avoid the appearance of spam, phishing, or other fraudulent activity. I summarized some of the subscription form abuse issues that we’re seeing across the web, and noted responses from Spamhaus and others involved in fighting this abuse. We’re working closely with ESPs and policy groups to continue to document, analyze and strategize best practices to provide industry-wide responses to these attacks.
I was pleased to note that Google is stepping up with a new program, Project Shield, to help journalists and others who are being targeted by these attacks by providing hosting and DDoS protections.
I’m also delighted to see some significant improvements in email client interactions and user experiences. I wrote a bit about some of those here, and I added my thoughts to Al’s discussion of a new user interaction around unsubscribing in the iOS 10 mail client, and I’ll be curious to see how this plays out across other mail clients.
For our best practices coverage, Steve wrote about global suppression lists, and the ways these are used properly and improperly to prevent mail to certain addresses. I wrote about using the proper pathways and workflows to report abuse and get help with problems. I also wrote about the ways in which incentivizing address collection leads to fraud. This is something we really need to take seriously — the problem is more significant than some bad addresses cluttering up your lists. It contributes to the larger landscape of fraud and abuse online, and we need to figure out better ways to build sustainable email programs.
Is there such a thing as a perfect email? I revisited a post from 2011 and noted, as always, that a perfect email is less about technology and more about making sure that the communication is wanted and expected by the recipient. I know I sound like a broken record on this point (or whatever the 21st century equivalent metaphor of a broken record is….) but it’s something that bears repeating as marketers continue to evolve email programs.
We had a bit of a discussion about how senders try to negotiate anti-spam policies with their ESPs. Is this something you’ve experienced, either as a sender or an ESP?
In Ask Laura, I covered shared IP addresses and tagged email addresses, questions I get fairly frequently from marketers as they enhance their lists and manage their email infrastructures. As always, we welcome your questions on all things email delivery related.
Censorship and free speech online
One of the things I discovered yesterday while looking at Krebs on Security was that Google Alphabet has a program to provide hosting and dDOS protection for journalists. Project Shield, as it’s called, is a free service for approved applicants that keeps up websites that might be taken down otherwise. Eligible organizations include those providing news, information on human rights and monitoring elections.
This is something I hadn’t heard of before and my only reaction is good for Google.
Look, we’ve gotten to the point where attackers have resources beyond the scope that most of us can imagine. It’s expensive even for large organizations to manage and pay for the level of protection they need.
Even more importantly a lot of very important work is done by individuals or small organizations. Brian is a prime example of that. He does an incredible job investigating online crime on his own time. His site and his information is an invaluable resource for many. Losing his site, and losing his information would leave a huge hole in the security community. There are other folks in other spaces who, like Brian, don’t have the resources to protect themselves but do have important things to say and share.
I’m glad to see Google committing their resources and skills to help organizations protect themselves. It’s so important that this work is done and we don’t lose voices just because they can’t afford hundreds of thousands of dollars a year.
There has been abuse and harassment online for as long as I’ve been here. But it seems recently the size and severity of attacks have increased. And a lot of service providers are struggling with how to manage it and what their responsibilities are.
A few weeks ago Facebook deleted an iconic photo from the Vietnam era due to child nudity in the photo. That decision was reversed and discussed in many, many different places. One of the most interesting discussion happened on a friend’s Facebook feed. Many of the participants work at various online providers. They have to make these kinds of decisions and create policy to do the right thing – whatever the right thing is. It was very interesting to be able to follow the discussion and see how many different issues FB and other online providers have to consider when creating these types of policies.
I thing the thing I have to confront the most about the internet is how big it is. And how crucial it’s become to all sorts of issues. Social media can be a cesspool of abuse, there’s no question. But it can also be a force for good. I’m glad companies like Google are stepping up to preserve the good parts of the internet.
Ongoing subscription form abuse
Last week Spamhaus posted information on the ongoing subscription attacks. They provided a more information about them that was not make public previously, including some information about the volume of mail some targets received.
Today SendGrid also blogged about this, going into a little more detail about why senders should care about this. They also provided a number of suggestions for how to mitigate the risk of being part of an attack.
There are a couple of things I think it’s important for folks to realize.
Spamhaus and subscription bombing
Spamhaus released a blog post today discussing the recent subscription bombing: Subscription bombing COI captcha and the next generation of mail bombs.
As I mentioned in my initial posts, this abusive behavior goes beyond spamming. This is using email to harass individuals. Spamhaus even mentions a potential service that can be used to do these kinds of mailbombing.
Things folks need to know is that this is not just about ESPs and commercial mail. One of the big targets was WordPress admin forms. As Spamhaus says:
Abuse, triage and data sharing
The recent subscription bombs have started me thinking about how online organizations handle abuse, or don’t as the case may be. Deciding what to address is all about severity. More severe incidents are handled first. Triage is critical, there’s never really enough time or resources to investigate abuse.
What makes an event severe? The answer is more complicated that one might think. Some of the things that ISP folks look at while triaging incoming complaints include:
Mandrill changes
Last week Mandrill announced that they were discontinuing their free services and all customers would be required to have a corresponding paid Mailchimp account.
Read MoreJanuary 2016: The Month in Email
 Happy 2016! We started off the year with a few different “predictions” posts. As always, I don’t expect to be right about everything, but it’s a useful exercise for us to look forward and think about where things are headed.
Happy 2016! We started off the year with a few different “predictions” posts. As always, I don’t expect to be right about everything, but it’s a useful exercise for us to look forward and think about where things are headed.
I joined nine other email experts for a Sparkpost webinar on 2016 predictions, which was a lot of fun (see my wrap up post here), and then I wrote a long post about security and authentication, which I think will be THE major topic in email this year both in policy and in practice (see my post about an exploit involving Trend Micro and another about hijacked Verizon addresses). Expect to hear more about this 2016 continues.
My other exciting January project was the launch of my “Ask Laura” column, which I hope will prove a great resource for people with questions about email. Please let me know if you have any questions you’d like to see me answer for your company or your clients — I’ll obscure any identifying information and generalize the answers to be most widely applicable for our readers.
In other industry news, it’s worth noting that Germany has ruled it illegal to harvest users’ address books (as Facebook and other services do). Why does that make sense? Because we’re seeing more and more phishing and scams that rely on social engineering.
In best practices, I wrote about triggered and transactional emails, how they differ, and what to consider when implementing them as part of your email program. Steve describes an easy-to-implement best practice that marketers often ignore: craft your mails so the most important information is shown as text.
I re-published an older post about SMTP rules that has a configuration checklist you might find useful as you troubleshoot any issues. And a newer issue you might be seeing is port25 blocking, which is important if you are hosting your own email senders or using SMTP to send to your ESP.
Finally, I put together some thoughts about reporting abuse. We work closely with high-volume abuse desks who use our Abacus software, and we know that it’s often not worth the time for an individual to report an incident – but I still think it’s worthwhile to have the infrastructure in place, and I wrote about why that is.
The truth matters.
 Call within the next 10 minutes…
Call within the next 10 minutes…
Consumers with last names starting with O – Z can call tomorrow…
Only 5 seats left at this price!
All of these are common marketing techniques designed to prompt consumers to buy. It’s not a new idea, create a sense of urgency and people are more likely to buy.
I think some marketers are so used to making outrageous claims to support their marketing goals, that it doesn’t occur to them that the truth matters to some people.
There’s almost no better way to get me to send in a spam complaint than to send me an email with a claim about how I opted in.
Example:
Random thoughts on reporting abuse
 On IRC today, someone mentioned an Ars Technica article discussing how a research team tried to contact Xfinity about a security flaw in their home security system.
On IRC today, someone mentioned an Ars Technica article discussing how a research team tried to contact Xfinity about a security flaw in their home security system.
Peeple, Security and why hiding reviews doesn't matter
There’s been a lot of discussion about the Peeple app, which lets random individuals provide reviews of other people. The founders of the company seem to believe that no one is ever mean on the Internet and that all reviews are accurate. They’ve tried to assure us that no negative reviews will be published for unregistered users. They’re almost charming in their naivety, and it might be funny if this wasn’t so serious.
The app is an invitation to online abuse and harassment. And based on the public comments I’ve seen from the founders they have no idea what kind of pain their app is going to cause. They just don’t seem to have any idea of the amount of abuse that happens on the Internet. We work with and provide tools to abuse and security desks. The amount of stuff that happens as just background online is pretty bad. Even worse are the attacks that end up driving people, usually women, into hiding.
The Peeple solution to negative reviews is two fold.
Mary Litynski Award winner Jayne Hitchcock
This morning the Messaging, Mobile and Malware Anti-Abuse Working Group announced the winner of the Mary Litynski Award.
Congratulations to Jayne Hitchcock of WHO@ for her work over the last 2 decades fighting online abuse and cyberstalking.
I’ve never actually met Jayne, but I do remember following her story in the late 90s. She started off trying to protect people from being scammed by Woodside Literary Agency. In return for her work to inform and protect people the principals of Woodside set out on a multi-year harassment campaign against her.
This was in the late 90s and the Internet was very new. There weren’t any laws. There weren’t really abuse desks. We had to protect each other. Law enforcement didn’t know what to do with problems. There weren’t any laws against harassment online. The word “cyberstalking” was created by a reporter when describing what was happening to Jayne.
Jayne has been a force for good online and she and her volunteers help people who are victims of abuse online and cyberstalking. She’s been instrumental in getting anti-cyberstalking laws passed and helping law enforcement understand why online abuse is an issue and that it should be addressed.
Anon whois information
I’ve talked before about reasons not to hide commercial domains behind whois proxies. Al found another one: if you use a proxies you cannot list your domains with abuse.net. Al has a good write up of whois, and why this is important. So go there and read it.
Read MoreDo you have an abuse@ address?
I’ve mentioned multiple times before that I really don’t like using personal contacts until and unless the published or official channels fail. I don’t hold this opinion just about resolving delivery issues, but also use official channels when reporting spam to one of my addresses or spam traps.
My usual complaints contain a plain text copy of the mail, including full headers and a short summary of the email address it was sent to. “This is an address that was part of a leak from…” or “This is an address scraped off my website. It’s been removed from the website since 2004” or “This address isn’t used to sign up for any mail.”
Sadly, there are a number of “legitimate” ESPs that don’t have or don’t monitor their abuse address. In some cases it’s an oversight or a break down of internal mail handling. But in most cases, it’s a sign that the ESP doesn’t actually handle abuse.
It’s frustrating to watch an ESP post long blog posts about “best practices” and “effective delivery” and “not spamming” and yet not be able to actually stop their own customers from spamming. It’s not even that I necessarily want them to disconnect their spamming customers (although that would be nice) but suppressing the address that I’ve told them was a spamtrap seems trivial. And yet, a month after my first complaint and weeks after escalating to a personal contact, I’m still getting spam.
The 5 things every ESP should do to handle spam complaints.
Policing customers
In yesterday’s post about Cloudflare and Spamhaus Fazal comments that Cloudflare may have been asked by law enforcement to leave the website up.
This does happen and it’s not totally out of the question that’s what is going on with this particular website. But I used the malware C&C as an example of the poor behaviour condoned by Cloudflare, it’s certainly not the only bad behaviour. There’s also the issue that Cloudflare disavows all responsibility for the behaviour of their customers.
Services, abuse and bears
A couple weeks ago I wrote a post about handling abuse complaints. As a bit of a throwaway I mentioned that new companies don’t always think about how their service can be abused before releasing it on the unsuspecting internet.
Today’s blog post by Margot Romary at the Return Path In the Know blog reminds me that it’s not always new companies that don’t think about abuse potential before launching services.
Report Spam button
Cloudmark has an interesting discussion about the Report Spam button and how it’s used.
Read MoreDealing with complaints
There are a lot of people who abuse online services and use online services to abuse and harass other people. But handling complaints and handling the abuse are often afterthoughts for many new companies. They don’t think about how to accept and process complaints until they show up. Nor do they think about how bad people can abuse a system before hand.
But dealing with complaints is important and can be complicated. I’ve written many a complaint handling process document over the years, but even I was impressed with the Facebook flowchart that’s been passed around recently.
In the email space, though, all too many companies just shrug off complaints. They don’t really pay attention to what recipients are saying and treat complaints merely as unsubscribe requests. Their whole goal is to keep complaints below the threshold that gets them blocked at ISPs. To be fair, this isn’t as true with ESPs as it is with direct senders, many ESPs pay a lot of attention to complaints and will, in fact, initiate an investigation into a customer’s practice on a report from a trusted complainant.
There are a lot of legitimate email senders out there who value quantity over quality when it comes to complaints. But that doesn’t mean their lists are good or clean or they won’t see delivery problems or SBL listings at some point.
Don't spam filter your role accounts
A variety of “amazon.com order confirmations” showed up in my inbox this morning. They were quite well done, looking pretty close to real Amazon branding, so quite a few people will click on them. And they funnel people who do click to websites that contain hostile flash apps that’ll compromise their machines (and steal their private data, login and banking credentials then add them to botnets to attack other sites and so on).
Not good. Just the sort of urgent, high-risk issue that ISP abuse desks really want to hear about. I sent email about it to the ISPs involved, including a copy of the original email. One of them went to iWeb, a big (tens of thousands of servers) hosting company.
This was the response:
Where do you accept reports?
One of the things that is most frustrating to me about sending in spam reports is that many ESPs and senders don’t actively monitor their abuse address. A few months ago I talked about getting spam from Dell to multiple email addresses of mine.
What I didn’t talk about was how badly broken the ESP was in handling my complaint. The ESP was, like many ESPs, an organization that grew organically and also purchased several smaller ESPs over the course of a few years. This means they have at least 5 or 6 different domains.
The problem is, they don’t effectively monitor abuse@ for those different domains. In fact, it took me blogging about it to get any response from the ESP. Unfortunately, that initial response was “why didn’t you tell us about it?”
I pointed out I’d tried abuse@domain1, abuse@domain2, abuse@domain3, and abuse@domain4. Some of the addresses were in the mail headers, others were in the ESP record at abuse.net. Three of those addresses bounced with “no such user.” In other words, I’d tried to tell them, but they weren’t accepting reports in a way I could access.
Every ESP should have active abuse addresses at domains that show up in their mail. This means the bounce address domain should have an abuse address. The reverse DNS domain should have an abuse address. The d= domain should have an abuse address.
And those addresses should be monitored. In the Dell case, the ESP did have an active abuse@ address but it was handled by corporate. Corporate dropped the ball and never forwarded the complaint to the ESP reps who could act on the spam issue.
ESPs and all senders should have abuse@ addresses that are monitored. They should also be tested on a regular basis. In the above case, addresses that used to work were disabled during some upgrade or another. No one thought to test to see if they were working after the change.
You should also test your process. If you send in a complaint, how does it get handled? What happens? Do you even have a complaint handling process outside of “count and forward”?
All large scale senders should have appropriate abuse@ addresses that are monitored. If you don’t, well, you look like a spammer.
Gmail abuse and postmaster addresses
A long time ago, Steve wrote a post about setting up abuse and postmaster addresses for Google hosted domains. Google has gone through a couple iterations of the interface since then, as you can see by the comment stream.
I checked with some people who have Google hosted domains and they have confirmed that abuse@ and postmaster@ addresses can be set up by creating a group. When you create the group you can then add yourself to the group and get the mail that comes into abuse@ and postmaster@.
The little things
It really amuses me when I get blatant spam coming from a network belonging to one of our Abacus customers. I know that the complaint will be handled appropriately.
It’s even better when the spam advertises the filter busting abilities of the spammer. I get a warm, fuzzy feeling to know that the spammer is going to be looking for a new host in the immediate future.
Have you audited your program lately?
A few months ago, I got spammed by a major brand. I know their ESP takes abuse seriously, so I sent a note into their abuse desk. It bounced with a 550 user unknown. I sent another note into a different abuse address, it bounced. I sent mail into their corporate HQ, it disappeared into a black hole. I eventually connected with their delivery person and he’d not seen hide nor hair of any complaint. Their entire abuse handling system had broken down and no one noticed.
In the recent past, I was dealing with a client’s SBL listing. We were talking about how their fairly clean subscription process ended up with multiple Spamhaus spamtraps on the list. They mentioned bounce handling, and that they’d not been correctly managing bounces for some period of time. Their bounce handling system was broken and no one noticed.
Last year, I was working with another client. They were looking at why some subscribers were complaining about unsubscribes not taking. A bit of poking at different forms and they realized that one of their old templates pointed to an old website. Their unsubscription form had broken and no one noticed.
Another client insisted that their engagement handling removed any addresses that didn’t open or click on mail. But after ignoring their mail for 6 months, they still hadn’t stopped mailing me. Their engagement handling was broken and no one noticed.
Periodic monitoring would have caught all of these things before they became a big enough problem to result in a Spamhaus listing, or recipient complaints, or lawsuits for failure to honor CAN SPAM. Unfortunately, many companies don’t check to make sure their internal processes are working very often.
Email marketing is not set and forget. You need to monitor what is happening. You need to make sure that your processes are still in place and things are still working.
Spamhaus and Gmail
Today’s been chock full of phone calls and dealing with clients, but I did happen to notice a bunch of people having small herds of cows because Spamhaus listed www.gmail.com on the SBL.
“SPAMHAUS BLOCKS GOOGLE!!!” the headlines scream.
My own opinion is that Google doesn’t do enough to police their network and their users, and that a SBL listing isn’t exactly a false positive or Spamhaus overreaching. In this case, though, the headlines and the original article didn’t actually get the story right.
Spamhaus blocked a range of IP addresses that are owned by Google that included the IP for www.gmail.com. This range of IP addresses did not include the gmail outgoing mailservers.
Spamhaus says
Should you respond to complaints
Should you ever contact someone who made an abuse complaint about your newsletter to find out why
Read More
Project Omnivore
Ben at Mailchimp has posted some information about Project Omnivore. This is a predictive system that not only predicts potential abuse, but can also be used to predict poor campaigns. Steve and I had a chance to see Omnivore in action when we were in Atlanta last fall, and were impressed by the accuracy for bad stuff. It seems, however, that Omnivore is useful to predict good behaviour as well.
Read MoreCompliance vs. Deliverability
Most people I know handling delivery issues for senders have some version of delivery or deliverability in their job title. But as I talk to them about what they do on a daily basis, their role is as much policy enforcement and compliance as it is delivery. Sure, what they’re telling customers and clients is how to improve delivery, but that is often in the context of making customers comply with relevant terms and conditions.
Some delivery folks also work the abuse desk, handling complaints and FBLs and actually putting blocks on customer sends.
I think the compliance part of the delivery job description that is often overlooked and severely downplayed. No one likes to be the bad guy. None of us like handling the angry customer on the phone who has had their vital email marketing program shut down by their vendor. None of us like the internal political battles to convince management to adopt stricter customer policies. All of these things, however, are vital to delivery.
Despite the lack of emphasis on compliance and enforcement they are a vital and critical part of the deliverabilty equation.
Google Apps – where's my abuse@
Most ISP feedback loops require you to demonstrate that you’re really responsible for your domain before they’ll start forwarding reports to you. The usual way that works is pretty similar to a closed-loop opt-in signup for a mailing list – the ISP sends an email with a link in it to the abuse@ and postmaster@ aliases for your domain, and you need to click the link in one or both of the emails to continue with the feedback loop signup process.
That’s mostly there to protect you, by making sure that someone else can’t get feedback loop messages for your domain. And it’s not too difficult to do, as you should already have an abuse@ and postmaster@ alias set up, and have someone reading the abuse@ alias.
But maybe you’re using Google Apps to host your corporate email, and that’s the domain you need to use for your feedback loops. So you go to create abuse and postmaster users, but it won’t let you – you just get the error Username is reserved for email list only. Uhm, what?
Google want to police use of domains hosted on their service, so they automatically set up abuse and postmaster aliases for your domain, and any mail sent to them is handled by Google support staff. You may well be happy with Google snooping on your abuse role account, but you really need to be able to read the mail sent to it yourself too.
So what to do? Well, the way Google set things up they actually create invisible mailing lists for the two role accounts, and subscribe Google Support to the lists. In older versions of Google Apps you could make those mailing lists visible through the user interface by trying to create a new mailing list with the same name, then simply add yourself to the mailing list and be able to read your abuse@ email.
But Google broke that functionality in the latest version of the Google Apps control panel, when they renamed email lists to “groups”. If you try and create a new group with the email address abuse@ your domain you’ll get the error Email already exists in this domain, and no way to make that list visible.
So, what to do?
Well, there’s a workaround for now. If you go to Domain Settings you can select the “Current Version” of the control panel, rather than the “Next Generation” version. That gives you the old version of the control panel, where all this worked. Then you can go to User Accounts, create a new email list delivering to abuse@ and add one of your users to the mailing list. You can then set the control panel back to “Next Generation” and have access to the mailing lists via Service Settings → Email → Email Addresses.
Hopefully Google will fix this bug, but until they do here’s the step-by-step workaround:
Alphabetical spammers
There have been a couple posts recently about a paper presented at the Fifth Conference on Email and Spam (CEAS). The paper showed how addresses beginning with different letters get different volumes of spam.
But this post is not really about the paper, although it is an interesting academic review of spam, it is more about a memory that the discussions triggered.
Long ago I was handling the abuse desk at the very large network provider. This was in the days before Feedback loops, so every complaint was an actual forwarded email from a recipient. Generally, we saw a couple dozen complaints about any individual spam problem. Not a huge volume by any means, but that meant that any volume of complaints was significant.
One afternoon I started seeing a spike in complaints about a customer who never received complaints before. I started looking a little deeper and discovered we had around 50 complaints about this mailing, many from people I knew, and all from individuals at domains that started with A. This was one of the few times we actually pulled the plug in the middle of a mailing.
I still remember going to my boss suggesting this was something to take action on now because we had over 50 complaints and they were still in the A‘s! The customer was mortified that the guaranteed opt-in list they purchased was so bad and promised never to spam again.
Have a good weekend everyone.