Recent Posts
Email Innovations Summit in May 2016
- laura
- Jan 15, 2016
I’ve been accepted as a speaker for the Email Innovations Summit in Las Vegas in May. This is a conference hosted by the folks behind the Only Influencers group and should be a great way to meet some of the leading minds in email marketing.
I’ll be speaking on some of the things I see changing in the email space and how that will affect email marketing as a whole. I think it will be great fun and look forward to meeting many of my OI colleagues.
Port25 blocking
- laura
- Jan 14, 2016
 A number of hosting providers are blocking outgoing port25. This has implications for a lot of smaller senders who either want to run their own mail server or who use SMTP to send mail to their ESP.
A number of hosting providers are blocking outgoing port25. This has implications for a lot of smaller senders who either want to run their own mail server or who use SMTP to send mail to their ESP.
Security vendors and trust.
- laura
- Jan 13, 2016
A big part of my predictions for 2016, that I’ll publish shortly, is that security is going to be a huge issue. I think we’re really going to see receivers expecting senders to have their houses in order when it comes to sending mail.
Of course, some filter companies need to get their houses in order to. Yesterday, a security researcher went public with problems in the TrendMicro anti-virus appliance. These vulnerabilities would let any email sender remotely execute code on the recipients machine with no interaction of the user. They also exposed all the passwords on the machine to the outside world.
Even worse, Trend doesn’t seem to understand the urgency to fix this. They have started releasing patches for the exploits, but there are significant problems with the patched versions as well.
If you’re a Trend user, you may want to consider other vendors for desktop security. I know that no security is perfect and that other vendors have problems, too. But shipping a password manager that exposes all passwords is just incompetence. It seems like a corporate lack of understanding of what their business is and how to actually create security software.
Even worse is that lack of urgency from the Trend folks as the security researchers are explaining the problem. I don’t care if the person receiving the report was the janitor, anything that says security exploit should be escalated to someone who can determine if the report is valid.
Compare Trend’s reaction to this to Juniper’s reaction to discovering a backdoor in their code in December. First off, Juniper found the exploit during a routine code review. That alone tells you Juiper is continually monitoring their code security. Second, Juniper was reasonably open about the issue, with executives posting blogs and security posting advisories talking about the issue. More importantly, they shared how they were going to fix it and prevent it from happening again.
Security is such a large issue right now. We have to be able to trust our vendors to do what they’re selling us. Every vendor is going to make mistakes and have vulnerabilities. No code and no developer is perfect. I do expect, though, that vendors will take exploits seriously and act fast in order to correct the problem. I’m not seeing that sense of urgency with Trend.
Spamhaus reports Verizon routing hijacked IPs
- laura
- Jan 11, 2016
Late last week Spamhaus published a blog post detailing their investigation into Verizon routing millions of IP addresses hijacked by spammers.
The Spamhaus blog post goes into some detail about what hijacked routing is.
Triggered and transactional emails
- laura
- Jan 8, 2016
 Earlier this week I was talking on IRC with some colleagues. There was some kvetching about senders that think transactional emails are the same as triggered emails. This led to discussion about whether transactional and triggered emails are the same. I don’t think they are, but it took a while for me to come up with why I don’t think they’re the same. It took even longer to come up with definitions I liked.
Earlier this week I was talking on IRC with some colleagues. There was some kvetching about senders that think transactional emails are the same as triggered emails. This led to discussion about whether transactional and triggered emails are the same. I don’t think they are, but it took a while for me to come up with why I don’t think they’re the same. It took even longer to come up with definitions I liked.
Transactional Emails: Emails sent in response to direct request by the recipient. Transactional emails are usually one-off emails. Transactional emails probably don’t need an unsubscribe link, although it may be a good idea to include one just to make people feel comfortable receiving them. Examples: password reset emails, receipts, tickets.
Triggered Emails: Emails sent in response to an action by a recipient. Triggered emails can be one-off, but can also be series of emails. Triggered emails should have an unsubscribe link, so people can stop the emails if needed. Examples: cart abandonment emails, after purchase surveys, followups to software installation.
The key difference is that in a transactional email, the recipient has asked for that particular email. In a triggered email, the recipient may very well want and respond to the email, but they didn’t ask for it.
There are, as always, some grey areas here. Is a welcome message transactional or triggered? Probably transactional, but they should always have an unsubscribe link.
What about software installation followups? We’ve been looking at some alternatives to our current time tracking software which involved me setting up accounts at multiple different SaaS providers. A couple of them had triggered welcome series. These emails let me know things I could do with the software, things I still needed to set up, and led me through the process of trying out their system.
This was mostly good, but not completely. One of the series didn’t have an opt-out link, though. That was somewhat annoying because I’d already decided the tracker didn’t do what we needed. I couldn’t make the mail stop. I think if there is one thing I’d say about mail is that senders should never force someone to receive their mail.
It’s tempting for senders to define all triggered emails as transactional. Since it’s a user action that caused the mail to be sent, it must be a transactional email. But a lot of triggered emails are triggered by actions the user doesn’t know will trigger an email. Cart abandonment emails are a good example of this, not every retailer has them and so users aren’t yet expecting to get an email if they drop stuff in their carts and then leave the site.
Overall, both transactional and triggered emails have their place in a healthy email program. But they shouldn’t be confused for one another and should be treated as separate mail streams.
10 experts in 50 minutes: predictions for 2016
- laura
- Jan 8, 2016
I’m thrilled to be one of the email experts speaking at the 2016 predictions webinar hosted by SparkPost.
Come join us!
Facebook scams move to LinkedIn
- laura
- Jan 6, 2016
There’s a fairly common Facebook scam where someone clones an account, then sends out friend requests to friends of that person. This actually happened to a friend over the holiday break. The only problem was that most of the folks who got friend requests were actually security people. Security people who thought it was very, very funny to play along with said scammer.
The scam account didn’t last long, partly because FB security is pretty good and partly because a few of the folks the scammer invited were FB employees. I’m sure, though, that for a brief moment the scammer thought he’d found the motherlode of scam victims.
Today I got a similar scam on LinkedIn. A very bare account with little in the way of information about who this was.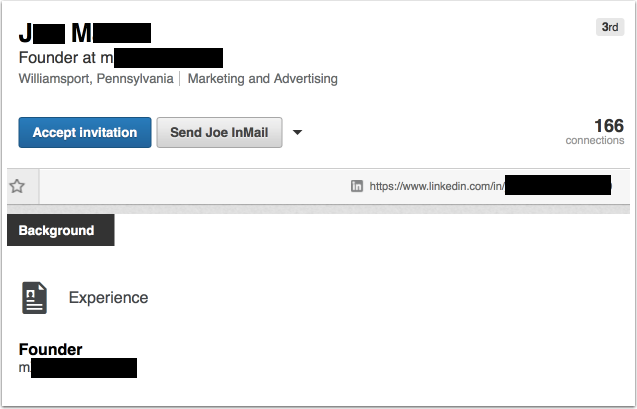
I don’t like connecting with these kinds of profile. But, the name does sound vaguely familiar. So I do a little Googling. And I find another LinkedIn profile for the same person, but this profile has a lot more info: A picture, a statement, 500+ connections, all the things one expects from a real person on LinkedIn.
So yes, Facebook scams have rolled over to LinkedIn. Be careful out there, folks. Pay attention to who you’re friending on all social media, not just FB or LinkedIn. Discretion is the better part of valor and all.
Random thoughts on reporting abuse
- laura
- Jan 6, 2016
 On IRC today, someone mentioned an Ars Technica article discussing how a research team tried to contact Xfinity about a security flaw in their home security system.
On IRC today, someone mentioned an Ars Technica article discussing how a research team tried to contact Xfinity about a security flaw in their home security system.
December 2015: The month in email
- laura
- Jan 4, 2016
Happy 2016! We enjoyed a bit of a break over the holidays and hope you did too. Here’s our December wrap up – look for a year-end post later this week, as well as our predictions for the year ahead. I got a bit of a head start on those predictions in my post at the beginning of December on email security and other important issues that I think will dominate the email landscape in 2016.
DMARC will continue to be a big story in 2016, and we’re starting to see more emphasis on DMARC alignment as a significant component of delivery decisions. I wrote a bit more on delivery decisions and delivery improvement here.
December in the world of email is all about the holidays, and this year was no exception. We saw the usual mix of retailers creating thoughtful experiences (a nice unsubscribe workflow) and demonstrating not-so-great practices (purchased list fails). We took a deeper look at the impacts and hidden costs of list purchasing – as much as companies want to expand their reach, purchased lists rarely offer real ROI. And on the unsubscribe front, if you missed our discussion and update on unroll.me unsubs, you may want to take a look.
Steve wrote a detailed post looking at what happens when you click on a link, and how you can investigate the path of a clickthrough in a message, which is useful when you’re trying to prevent phishing, fraud, and other spam. In other malicious email news, the CRTC served its first ever warrant as part of an international botnet takedown.
In other industry news, some new information for both ESPs and recipients interested in feedback loops and a somewhat humorous look at the hot-button issues that divide our ranks in the world of email marketing. Please share any we may have missed, or any other topics you’d like us to address.
Doing it right
- steve
- Dec 29, 2015
It’s that time of the year – marketers send more email than usual, recipients unsubscribe from their lists.
Clicking on the unsubscription link in the email I just received took me to an unsubscription landing page. The box for my email address was prepopulated based on the cookie in the unsubscription link, the default setting is to unsubscribe me from all mail from the sender and just clicking the sole button on the page will unsubscribe me.
It offers me an alternative to unsubscribing from everything – letting me receive just the content I want. It does that immediately on the unsubscription landing page (rather than suggesting I go to a subscription center or, worse, requiring I click on a different link in the mail originally). And it tells me the important things about the newsletters I might want to subscribe to – what they’re about and how often they’re sent.
This isn’t anything particularly special, but sometimes it’s nice to highlight someone who is doing it right.
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Backus-Naur Form
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcc
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- BIMI
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cabbage
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- CFWS
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- DMARC
- DNS
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Strategy
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- GDPR
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- IPv4
- IPv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Message-ID
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Needs Work
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Re-Engagement
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Replay
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- RFC
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- SPF
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Undisclosed Recipients
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb