Recent Posts
iOS List Unsubscribe Functionality
- laura
- Sep 26, 2016
Al did a great post over on Spamresource about the how the new list unsubscribe function in the default mail client from iOS10. What’s been interesting to me is how much I’m hearing from ESP folks about how their customers want it gone.
If you don’t know what we’re talking about, in the default mail client on iOS10, Apple is now offering a way to unsubscribe from list mail by placing an unsubscribe link at the top of the message.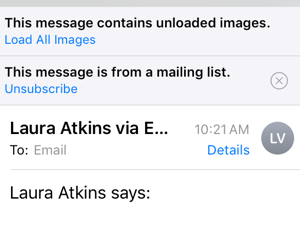
As you can see, this isn’t just for commercial mail, it’s in place for every mailing list that has a List-Unsubscribe header. (This is a screenshot from something I posted to OI this morning). For me, it’s somewhat intrusive. I’m on a lot of discussion lists – technical, marketing, business and even a couple social ones. Reading them on my phone has become a challenge, as every email in a thread contains the “unsubscribe” button now.
Luckily, you can dismiss the message for all posts to that mailing list by hitting the ⮾⮾⮾⮾x. Interestingly, once you’ve turned it off there seems to be no way to turn it back on for that list.
Senders have different complaints, however, they do not have to do with intrusiveness or usability issues.
I’ve heard complaints about placement and about how easy it makes it to unsubscribe. One person even stated that everyone knows the place for an unsubscribe is at the bottom of a message and it should never be at the top of a message. I find these arguments unpersuasive. Unsubscribing should be easy. Unsubscribing should be trivial. People should be able to stop getting mail on a whim. Particularly here in the US, where unsolicited mail is legal, being able to quickly opt-out is the only thing keeping some of our mailboxes useful.
I’ve also heard some concerns that are a little more understandable. One company was concerned that unsubscribes go directly to their ESP rather than directly to them. This is a somewhat more understandable concern. Good senders use unsubscribes as part of their KPIs and as part of their campaign metrics. They know how much an unsubscribe costs them and will use that as part of their metrics for defining a successful campaign. Still, though, it’s not that big a concern. ESPs are already handling these kinds of unsubscribes from providers like gmail and hotmail.
Almost 7 years ago I blogged about a sender who wanted an unsubscribe link in the email client. It was a bit of snark on my part. The interesting part, though, is that some senders want unsubscribe mediated in the client and others things it’s horrible. I think this tells me that there’s no universal right answer. It Depends might be the most hated statement in deliverability, but it is the absolutely the reality of the situation.
Global Suppression Lists
- steve
- Sep 23, 2016
Global Suppression List.
Pander File.
Screamers List.
Whatever you call it, it’s the list of email addresses you suppress from every mailing.
If you’re an ESP, this is the list of people who you never, ever want to send email to – and I’m talking about ESP-wide global suppression lists here, not the suppression lists maintained per-customer.
Global suppression lists are a vital tool to have, as it’s the only way you can comply with requests like “Never mail me again.” – and failing to comply with those will lead to, at best, irritation, yelling and blocking, and at worst legal action.
But it’s only the right tool for suppressing mail in a few cases. One obvious one is when someone specifically requests no more mail, ever, through your system. Another is when there’s a technical reason (you never want to send mail to autoresponders, for instance), or a legal reason (pending litigation, or an incompatibility between the mail you send and a specific jurisdiction).
And there are a very few people who just cause way too much support overhead when you send them email – that’s the origin of the term screamer list, I’m sure.
But it’s not what you should be reaching for in response to spam complaints, even heated ones, or feedback loop hits. A spam complaint is a sign that your customer is probably doing something wrong, and that this recipient doesn’t want that customers mail. A feedback loop hit says that this recipient doesn’t want that customers mail (and, statistically may indicate that your customer has a problem).
Neither of them is a sign that the recipient doesn’t want mail from any of your customers. You definitely wouldn’t want one of your customers sending spam to cause mail from all of your customers to be blocked – so why would you let a complaint about one of your customers block mail to that recipient from all your customers?
(We’ve occasionally come across ESPs who have preemptively blocked all mail to addresses @wordtothewise.com, for no clear reason. When our clients discover that their ESPs are silently discarding our attempts to subscribe to their mailing lists it doesn’t do much for that ESPs reputation in our clients’ eyes.)
And whatever you do, don’t respond to a spam complaint telling them you’ve added them to a global suppression list. That says several things, to an already annoyed person. It tells them that you’ve just broken their subscriptions, past or future, to your other customers. And by “fixing” the spam problem for this one recipent in this way it suggests that you’re not actually going to do anything to deal with the customer they’re complaining about. Nothing about this can end well.
Instead, tell them that you’ll make sure they don’t receive any further mail from that customer, and that you’ll talk with the customer and take action that you deem appropriate. (And then do that).
P.S. Does anyone know the origin or etymology of the term “pander file”?
Security issues affect us all
- laura
- Sep 22, 2016
I’ve been talking about security more on the blog. A lot of that is because the security issues are directly affecting many senders. The biggest effect recently has been on companies ending up on the SBL because their signup forms were the target of a subscription attack. But there are other things affecting online spaces that are security related. Right now not much of it is affecting email senders, but it’s good to be aware of.
DDOS attacks
There has been an increase in DDOS attacks against different companies and network. Some of the online game sites have been targeted including EA, Blizzard and others. A group called PoodleCorp is claiming responsibility for those attacks.
Another set of DDOS attacks hit Brian Krebs’ website this week. The site stayed up, but Akamai has told Brian they can no longer host his website. His website is down for now and the foreseeable future.
While this activity doesn’t affect marketers directly, it does tell us that there is active development happening on the less legal side of the internet. The volumes of the recent attacks have sent records. They’re also changing in scope and including new kinds of traffic in an effort to knock sites offline. Even more concerning, they appear to be systematically attempting to discover defenses in order to attack the internet as a whole.
Increase in Spam
Spam has been on the decrease over the last few years. Many of us were treating it as a mostly-solved problem. But a new report from Cisco Talos shows that trend is reversing and spam levels are increasing. Current levels are approaching those last seen more than 5 years ago. Cisco Talos has used a number of different sources of data, all showing an increase in spam directly and indirectly.
Use the form…
- laura
- Sep 21, 2016
A lot of senders get frustrated with the time it can take to get a response from some ISPs. It’s totally understandable, for a lot of companies delivery problems are all hands on deck level problems. They want them fixed and they want them fixed IMMEDIATELY. They want feedback that their issue is being addressed. They want to know someone at the ISP knows there is a problem.
I’ve talked before about visiting my friend Anna and watching her laptop screen explode with IMs from senders who wanted help with an AOL issue. She’s awesome and conscientious and tried to address all of those issues as fast as she could. She did want senders to feel like their issues were important and that someone inside AOL cared about the mail blocks.
I was always a strong advocate for following the official pathways for addressing problems. That was the whole point of the 2009 blog post. These days it’s easier to do than it ever was. Many ISPs have forms and process around handling delivery issues. This is good! In the past getting an answer to “why is my mail blocked” required knowing the right people. Now, it’s not about who you know. The ISPs and filtering companies who are open to senders have postmaster pages, unblock forms and official request channels. Those that don’t have those channels have made certain business decisions to not provide support for senders.
Despite the availability of webforms and knowledge bases and detailed information, a lot of people still think that the only way to get attention or get an issue addressed is to get someone on the phone. It’s not, though.
ISPs have their processes. If you want things handled quickly use those processes. Even in the places where very helpful reps are, they can’t (on order of lawyers and executives) help people unless there is a ticket already open.
Always, always use the recommended processes before trying to find “a real person.” Most of the time your issue can be solved faster if you fill out the form than if you hunt around for a person. In the worst case, all that time will be wasted as the person in question will tell you to fill out the form.
Upcoming events
- laura
- Sep 20, 2016
Next month I’ll be in London for the Email Innovations Summit. This will be an updated version of what you need to know to talk with technical folks.
In early December I’ll be doing a DMA webinar discussing the subscription bombings. That’s still in the works.
I’m looking at some events for next year. I am planning on being at M3AAWG in San Francisco in February.
I’m looking at others, too. What are your favorite events?
Ongoing subscription form abuse
- laura
- Sep 20, 2016
Last week Spamhaus posted information on the ongoing subscription attacks. They provided a more information about them that was not make public previously, including some information about the volume of mail some targets received.
Today SendGrid also blogged about this, going into a little more detail about why senders should care about this. They also provided a number of suggestions for how to mitigate the risk of being part of an attack.
There are a couple of things I think it’s important for folks to realize.
Spamhaus and subscription bombing
- laura
- Sep 17, 2016
Spamhaus released a blog post today discussing the recent subscription bombing: Subscription bombing COI captcha and the next generation of mail bombs.
As I mentioned in my initial posts, this abusive behavior goes beyond spamming. This is using email to harass individuals. Spamhaus even mentions a potential service that can be used to do these kinds of mailbombing.
Things folks need to know is that this is not just about ESPs and commercial mail. One of the big targets was WordPress admin forms. As Spamhaus says:
Mail Client Improvements
- laura
- Sep 16, 2016
There’s been extensive and ongoing development of email through the years, but much of it has been behind the scenes. We were focused on the technology and safety and robustness of the channel. We’re not done yet, but things are much better than they were.
The good part of that is there is some space to make improvements to the inbox as well. Over the last few months there have been a number of announcements from different mail client providers about how they’re updating their mail client.
Responsive design just got easier at Gmail
- laura
- Sep 14, 2016
Today Gmail announced they are supporting media queries in Gmail and Google Inbox. This should simplify the creation of emails for multiple platforms. The full list of supported rules can be found on the Google Developer Site.
Read MoreMicrosoft deprecating SmartScreen filters
- laura
- Sep 13, 2016
At the beginning of the month Microsoft announced that they were deprecating the SmartScreen filters used by the desktop Microsoft mail clients. These are the filters used in Exchange and various version of Outlook mail. This is yet further consolidation of spam filtering between the Microsoft free webmail domains, Office365 hosted domains and self hosted Exchange servers. The online services (hotmail.com, outlook.com, Office365, live.com, etc) have been using these filters for a while. The big change now is that they’re being pushed down to Exchange and Outlook users not hosted on the Microsoft site.
EOP was developed for Outlook.com (and friends) as well as Office365 users. From Microsoft’s description, it sounds like the type of machine learning engine that many providers are moving to.
Microsoft has published quite a bit of information about these filters and how they work on their website. One of the best places to start is the Anti-spam Protection FAQ. Something senders should pay attention to is the final question on that page: “What are a set of best outbound mailing practices that will ensure that my mail is delivered?” Those are all things deliverability folks recommend for good inbox delivery.
Poking around looking at the links and descriptions, there is a host of great information about spam filtering at Microsoft and how it works.
A page of note is their Exchange Online Protection Overview. This describes the EOP process and how the filters work.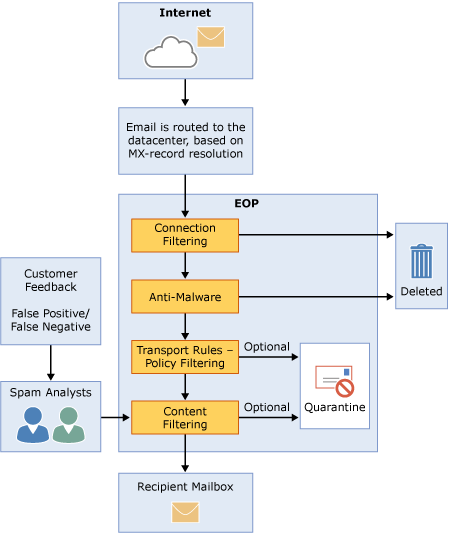
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Backus-Naur Form
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcc
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- BIMI
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cabbage
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- CFWS
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- DMARC
- DNS
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Strategy
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- GDPR
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- IPv4
- IPv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Message-ID
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Needs Work
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Re-Engagement
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Replay
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- RFC
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- SPF
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Undisclosed Recipients
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb