Recent Posts
It's that time of year
- laura
- Dec 21, 2016
I’m winding down blogging through the next week or so. I have a lot to say and blog about in the coming year, but I don’t think I’m alone in saying good bye and good riddance to 2016.
Happy Holidays to everyone, whatever events you may celebrate. I have to admit, it doesn’t feel very holiday around here. Part of that is we cut the cord a few months ago and we’ve not been subjected to the unending stream of Nutcracker music during commercials. We’ve also not been volunteering as stage crew for the local ballet school’s Nutcracker performance. There’s a definite dearth of Nutcracker music, which makes it seem less like the holiday season.
We did get our tree up this past weekend. I’ve got to admit, I’m really impressed the camera in my iPhone 7. It makes our tree look very festive (with a little help from Luminar)
Happy Holidays and a bright, shiny new year.
Poor delivery at Gmail but no where else
- laura
- Dec 21, 2016
I’ve mentioned before that I can often tell what ISP is making filter changes by what my calls are about. The last few weeks it’s been Gmail where folks are struggling to get to the inbox. One of the things most clients and potential clients have mentioned is that they’re not having any problems at the other major ISPs.
Read MoreListbombing Webinar
- laura
- Dec 16, 2016
Earlier this week I gave a webinar hosted by the EEC and the DMA discussing the listbombing problem. They will be making the recording available later this week and I will link to it then.
I wish I could say the issue was done and over with and that it was something we don’t have to worry about any longer. Unfortunately, that’s just not the case. Attacks are ongoing. Many of them are being caught and mitigated, but they’re still occurring.
We can’t let up our guard, though. Attackers will adapt to the mitigations and negate them.
And remember, listbombing is a sign that your subscription process is not collecting accurate data. If Evil Bob or Dumb Bob can give you Real Bob’s address then your data is all suspect. The problem is somewhat in the form, but it’s also in the whole process. What steps can you take to verify data without creating too much friction in the process?
This is an opportunity for forward thinking companies to reconsider their subscription and address acquisition processes. How do we get Bob’s address and information without Evil Bob or Dumb Bob giving us bad data and without contributing to the overall abuse online.
Is your website up? Are you sure?
- steve
- Dec 15, 2016
“What would you do for 25% more sales?”
It’s panicked gift-buying season, and I got mail this morning from Boutique Academia, part of their final push before Christmas.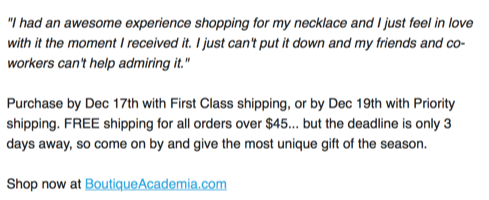
They’re hoping for some Christmas sales in the next three days. They do make some lovely jewelry – ask Laura about her necklace some time – so I clicked on their mail.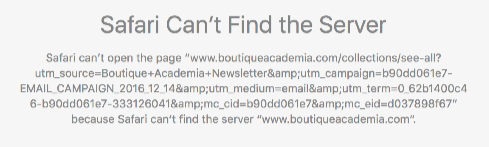
That’s not good. I like Boutique Academia, and fixing email and dns problems is What We Do, so I took a look.
Safari isn’t quite as bad with not-exactly-truthful error messages as Internet Explorer, but I still don’t really trust it. Perhaps the problem is with the click-tracking domain in the email, rather than with boutiqueacademia.com? So I open the base page at http://boutiqueacademia.com, get redirected immediately to https://www.boutiqueacademia.com – which fails to load.
OK, start with the basics. DNS.
DKIM Canonicalization – or – why Microsoft breaks your mail
- steve
- Dec 12, 2016

One of these things is just like the other
Canonicalization is about comparing things to see if they’re the same. Sometimes you want to do a “fuzzy” comparison, to see if two things are interchangeable for your purposes, even if they’re not exactly identical.
As a concrete example, these two email addresses:
Ask Laura: Should we confirm unsubscribes?
- laura
- Dec 9, 2016
Dear Laura,
We have some questions about best practices for unsubscribes. Our ESP uses the List-Unsubscribe header by default on every email. I’m not familiar with this, and I have some questions for you.
First, do you think this is a good idea? Should we always use it, or just for certain emails? Should we use the mailto:link or link to a web site to unsubscribe?
We were also asked about double opt-out and if we should do it. We’re thinking that if someone clicks on the unsubscribe link they would be directed to a site displaying a message such as “Sorry to see you go. We have sent an email out for you to fully unsubscribe from the mailing list”. They then have to open the email and click on the link. Do you recommend doing this? Are there anti-spam regulations that this might violate?
And then, once someone unsubscribes (either with double opt-out or not), should we send out some sort of email confirmation? We currently do not, but we’re thinking of sending something like “Sorry to see you go. If you unsubscribed accidentally please click here to re-subscribe.” What do you think?
Thanks,
Breaking Up Is Hard to Do
Industry news
- laura
- Dec 7, 2016
Just some stuff going on around email that probably merit a mention but not a whole blog post.
Next Tuesday at 1 eastern I’ll be giving a webinar on the subscription bombing and discussing what companies can do to mitigate the problem.
Google is working on new “invisible” captchas, that separate out humans from bots without humans having to do anything.
EmailonAcid created an interactive puzzle email.
Return Path acquired Email Copilot. Then laid off approximately 60 employees citing restructuring (no links for this one, but emails were sent to customers and someone forwarded me a copy).
Mailchimp sent 1.5 billion emails on Black Friday, and published stats and information about how well they delivered and performed.
Outreach or spam?
- laura
- Dec 6, 2016
This showed up in my mailbox earlier today: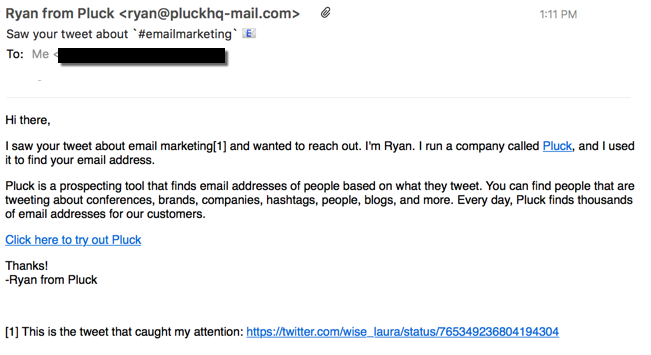
The tweet in question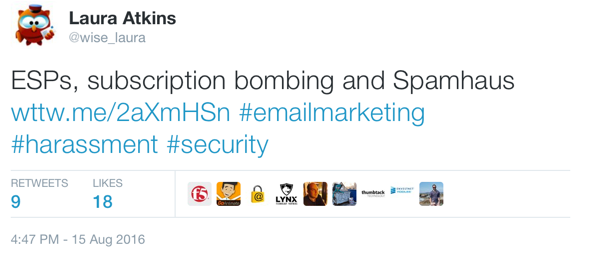
From Crunchbase: “Pluck is an email prospecting tool that gives you the email addresses of the people tweeting about subjects related to your business.”
Prospecting: another name for spamming. Look, I know that you want to sell you’re newest, greatest product to the world. But just because I tweet something with a # that you think is relevant to your product doesn’t mean that I want to get your spam. I also know it’s hard to get attention and find prospects; I’m a small business owner, too and I need to market my own services. But spamming isn’t a good idea. Ever.
There’s been a significant increase in this kind of spam “to help your business” lately. It’s a rare day I don’t get something from some company I’ve never heard of trying to sell me their newest product. It might be something if they tried a contact or two and then went away. But they’ll send mail for weeks or months without getting an answer. Look, silence IS an answer and it means you need to go away and leave your prospects alone.
Unfortunately, there are services out there that sell a product that let you “automatically follow up” with your prospects. Pluck up there uses one of them, as that’s who’s handling all the links in the message. In fact, if you go to the bare domain (qcml.io) they talk a good anti-spam game. “Die, spammers, die.” I reported the message to them. I’m not expecting them to actually do anything, and I’m not expecting a response.
It’s just spam under another name. There’s no pretense that it’s anything else. Even if it’s sent in a way that makes it look like a real person typed the message, like QuickMail offers. “All emails will come straight out of your personal inbox as though you typed them yourself.” As if you typed them yourself.
The worst part is there’s no real way to stop the mail. I can’t unsubscribe. The companies selling the software don’t provide any guidance to their customers about what the law requires. Take the message from Pluck that started the post. It violates CAN SPAM in multiple ways. Moreover, the address they used is not publicly associated with my twitter handle, which means they’re doing some harvesting somewhere. That means treble penalties under CAN SPAM.
I could reply and ask them to stop mailing me. I’ve done that a couple times with a message that says, “Please don’t email me any more.” I’ve got to tell you, some people get really mad when you ask them not to email you. Some just say yes, but others are really offended that you asked them to stop and get abusive. It’s gotten to the point where I don’t ask any more because of that one person who decides to harass, threaten and scream at me. Sure, it’s maybe 1 in 5, but I don’t have the time or energy to figure out who is going to be receptive and who isn’t. I don’t have time for that. No one has time for that.
I’m expecting that filters are going to catch up eventually and these types of mail will be easier to filter out. Until then, though, small business owners like myself are stuck in a place where we have to deal with spam distracting us from our business. At least I get blog content out of it.
November 2016: The Month In Email
- laura
- Dec 2, 2016
Happy December! Between #blackfriday, #cybermonday & #givingtuesday, pretty much everyone in the US has just survived a week of email from every brand and organization they’ve ever interacted with. Phew.
Is this still the best strategy for most senders? Maybe. But it’s always important to be adaptable and continue to evaluate and evolve your strategy as you move through the year.
As always, I continue to think about evolving our own strategies, and how we might best support senders and ESPs. One of the challenges we face when we talk to senders with deliverability questions is that so many of our answers fall into a nebulous “it depends” zone. We’re trying to articulate new ways to explain that to people, and to help them understand that the choices and details they specify at each point of their strategic planning and tactical execution have ramifications on their delivery. While “it depends” is still a correct answer, I’m going to try to avoid it going forward, and instead focus on exploring those choices and details with senders to help them improve deliverability.
In our community of deliverability and anti-abuse professionals, we are — as you’d expect — quite sensitive to unsolicited email that targets our industry. When an email circulates, even what seems like a reasonably well-thought-out email, it occasionally does not land well. Worse still are the various email-related product and service providers who try to legitimize B2B sales messaging as if it is something other than spam.
The takeaway from these discussions for senders is, as always: know your audience. This post about research from Litmus on millennials and spam is a great example of the kinds of things you might consider as you get to know your audience and how they prefer to communicate.
We also had a presidential election this month, one that made much of issues related to email, and it will be interesting to see how the candidates and parties use the email data they collected going forward.
In industry and security news, we saw over a million Google accounts breached by Android malware. We also saw some of the ramifications of a wildcard DNS entry from a domain name expiration — it’s an interesting “how things work” post if you’re curious. In other “how things work” news, we noted some of the recent changes AOL made to its FBL.
I answered an Ask Laura question about dedicated IP pools, and I have a few more queued up as well. As always, we want to know what questions are on the minds of our readers, so please feel free to send them over!
Google accounts breached
- laura
- Dec 1, 2016
Over 1 million Google accounts breached by Android malware.
There are some folks I know who really can’t understand why I stick with Apple over Android. The above issue is a big one. Doing what we do, security is a major consideration. I don’t need my accounts, or other accounts I have access to, compromised. It’s not that Apple is 100% compromise proof, but there are more checks and balances in the pipeline.
On the deliverability front, I had a recent interaction with someone from iCloud. This is a colleague I’ve worked with for years now, following him through multiple job changes. A client was having some delivery issues with a shared IP, so I was asking if he could send me some data to help track down the problem customer. I have a habit of asking for subject lines when I’m trying to get data. It’s usually enough for an ESP to track down the problem, and they’re not a way for folks to track down spamtraps or recipients. The answer I got back was sorry, they couldn’t give me any information at all, even something minor like a subject line.
Apple takes user privacy seriously and are doing a lot to protect their users. Does that mean I spend too much money on hardware I could buy cheaper? Perhaps. But, I’ll pay a little more to work with a company that puts privacy at the center of their product suite.
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Backus-Naur Form
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcc
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- BIMI
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cabbage
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- CFWS
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- DMARC
- DNS
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Strategy
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- GDPR
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- IPv4
- IPv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Message-ID
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Needs Work
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Re-Engagement
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Replay
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- RFC
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- SPF
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Undisclosed Recipients
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb
