Recent Posts
More on AOL transition to Oath Infrastructure
- laura
- Feb 9, 2018
AOL posted on their blog today about changes to DMARC reporting and FBL messages as they continue to transition domains to the OATH infrastructure. As AOL domains go to the new infrastructure, DMARC reports for those domains will be included in the existing Yahoo DMARC reports.
After the MX migration is done, they’ll start migrating the actual user mailboxes. Right now, FBL messages for AOL properties are coming from AOL and will continue to do so until the actual mailbox is transitioned to the new infrastructure. Once the mailbox is transitioned, then any FBL emails from that address will come from the Yahoo infrastructure. The blog post at AOL suggests signing up for both AOL and Yahoo FBLs during this transition phase.
It does bring up an interesting question as to whether or not the combined FBL is going to be IP based, DKIM based or a mix of both. It sounds like at least during some part of the consolidation there will be a DKIM only FBL. It could be that there will be some expansion to an IP system in the future. Or, it could be that all FBLs from AOL addresses will be based on DKIM domain.
Where to get deliverability help
- laura
- Feb 7, 2018
There are lots of places to get deliverability help, I thought I’d list some of them here so I have a post to point people to.
Of course, we provide deliverability consulting services and have done since 2001. Our customers are mostly large companies sending millions of emails a month. I focus mostly on complex problems that other deliverability folks haven’t solved. Overall I focus on understanding client programs and business needs as well as current deliverability situation. Once I have a picture of a client’s program, I craft solutions that work with their business processes and get mail to the inbox. We don’t sell tools or certification. Instead, we work with our clients to help them fix delivery and teach them how to analyze the data they already have.
The nature of the work I do is intensive and I limit the number of clients I have in order to provide personalized service. But that’s OK! We have 2000+ blog posts to answer questions. And, there are lots of other companies that provide deliverability help. Here’s a partial list of places to look for resources.
List-Unsub header
- laura
- Feb 6, 2018
Benjamin asked in the comments where in the interface the “unsubscribe” or “block” popup appeared. This is the dialog box Microsoft uses when the add the “unsubscribe here” link at the top of a message. Screenshots taken today from my Hotmail account: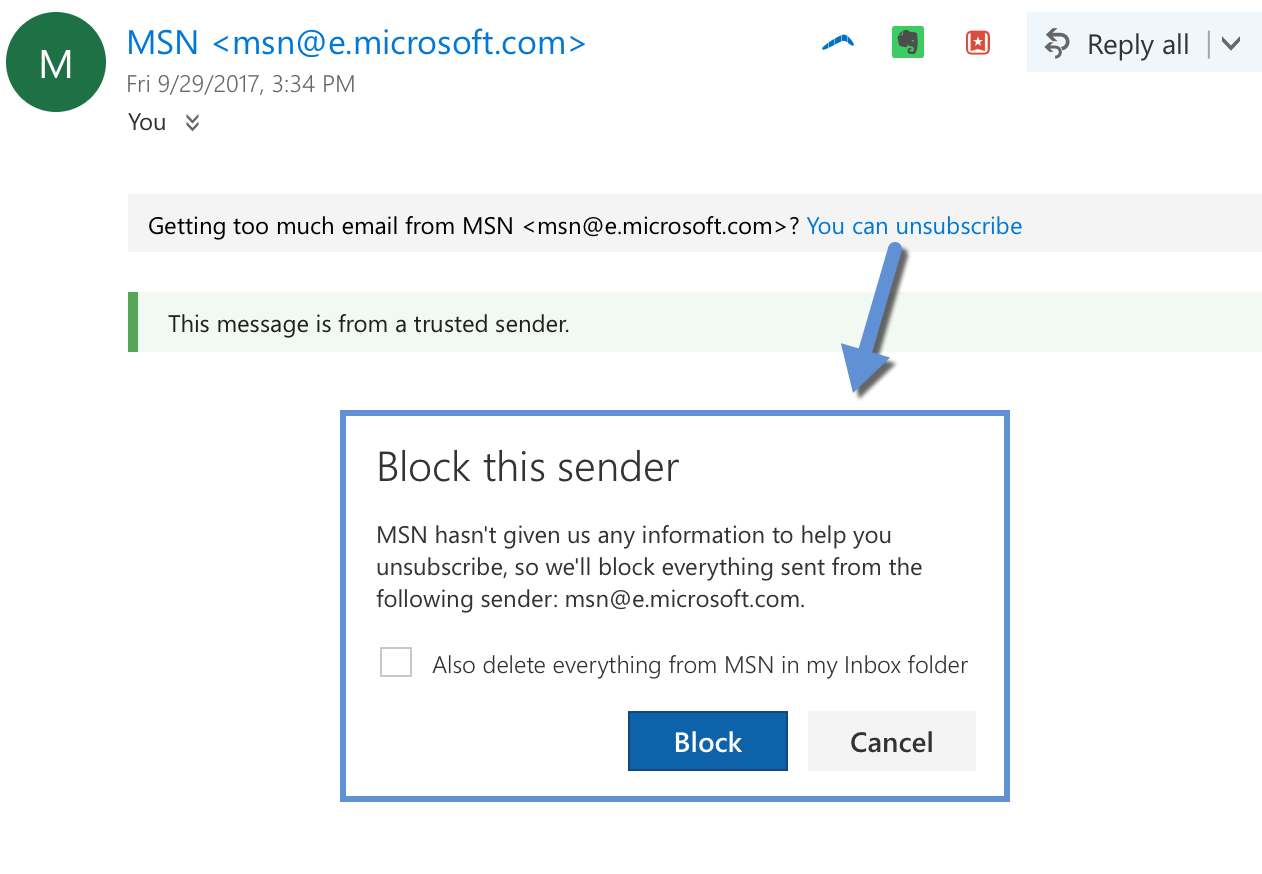 At this point we have 3 of the major webmail providers (Yahoo, Microsoft, Gmail) using List-Unsubscribe headers and at least one mobile client (Apple Mail). 20 years on it seems List-Unsubscribe is finally gaining traction.
At this point we have 3 of the major webmail providers (Yahoo, Microsoft, Gmail) using List-Unsubscribe headers and at least one mobile client (Apple Mail). 20 years on it seems List-Unsubscribe is finally gaining traction.
Notice, too, that ISPs hold their own mail to the same standards as outside mail. This really is Microsoft offering to let me block everything from MSN News.
GDPR and Whois data
- laura
- Feb 3, 2018
For folks who aren’t following the discussion about whois records and GDPR compliance there’s a decent summary at vice.com: What Is Going to Happen With Whois?
Read MoreYahoo List-Unsub header
- laura
- Feb 2, 2018
Last week some folks were mentioning a spike in unsubscribes from Yahoo. This is being investigated.
Microsoft using the List-Unsubscribe header
- laura
- Feb 1, 2018
An interesting observation from Brian Curry about how Microsoft is using the List Unsubscribe header in their interface. The short version is that Microsoft is only supporting mailto: links. They’re ignoring any List-Unsubscribe links that are a URL.
Here are some screenshots. When the sender is using a List-Unsubscribe <http://> header, Microsoft states that there is no information on how to help the user unsubscribe, so the offer to block the sender instead. Like in these two messages.

When the List-Unsubscribe header uses a mailto: link, Microsoft uses completely different language in the popup and does let the user know any future mail will go to the junk folder.

AOL MX Change update
- laura
- Jan 29, 2018
The AOL postmaster team posted some information about the upcoming MX transition on their blog.
Read MoreCollecting email addresses
- laura
- Jan 26, 2018
One of the primary ways to collect email addresses is from website visitors, and it’s actually a pretty good way to collect addresses. One of the more popular, and effective, techniques is through a pop-up window, asking for an address. Users need to provide an address or click a “no thanks” link or close the window. I’ve noticed, though, that many companies drop something passive aggressive in their “no thanks” button. “No, thanks, I don’t want to save money.” “I don’t need workout advice.”
Read MoreSocial media connections are not opt-ins
- laura
- Jan 25, 2018
It seems silly to have to say this, but connecting on social media is not permission to add an address to your newsletter or mailing list or prospecting list or spam list. Back in 2016, I wrote:
Read MoreStill with the Microsoft problems
- laura
- Jan 24, 2018
We took a quick trip to Dublin last week. I had every intention of blogging while on the trip, but… oops. I did get to meet with some clients, and had a great dinner while discussing email and delivery.
Coming back, I see a lot of folks still reporting delivery problems to Microsoft properties. I’ve been operating under the assumption this was temporary as kinks were worked out after the migration. I’m still pretty convinced not all of the problems are intentional. Even the best tested code can have issues that only show up under real load with real users. Reading between-some-lines tells me that the tech team is hard at work identifying and fixing issues. There will be changes and things will continue to improve.
With all that being said, I think it’s important to realize that delivering to the new system is not the same as delivering to the old system. This is a major overhaul of their email handling code, representing multiple years worth of planning and development inside Microsoft. It’s very likely that not all of the current delivery problems are the result of deployment. Some of the problems are likely a result of new standards and thresholds for reaching the inbox. What worked a year ago to get into the inbox just doesn’t any more.
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Backus-Naur Form
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcc
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- BIMI
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cabbage
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- CFWS
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- DMARC
- DNS
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Strategy
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- GDPR
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- IPv4
- IPv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Message-ID
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Needs Work
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Re-Engagement
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Replay
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- RFC
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- SPF
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Undisclosed Recipients
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb