Recent Posts
Don't wait to address delivery problems
- laura
- Jul 9, 2014
One of the worst ways to deal with blocking issues is to ignore them and hope your mail magically moves from the bulk folder back into the inbox. While this does happen as ISPs and filter companies update their filters, it’s not that common and it’s usually the result of a sender actually cleaning up their sending processes and improving the quality of the mail they send.
Do not ignore blocks. What I generally tell people is that it takes at least as long to repair a bad reputation as it took to get that bad reputation in the first place. If you wait months before actually addressing delivery problems, you’re not going to make a change and have the filters react in hours.
This doesn’t mean that every block is a business crisis. Blocks happen and they do go up and down based on thresholds and automatic monitoring scripts and content. But if a block happens consistently for 4 or 5 days in a row it is time to look at what you’re doing. Don’t just focus on the sidelines and little stuff, either. Look at your marketing program and the mail you’re sending.
The DMA: Email marketing or spam?
- laura
- Jul 7, 2014
A few weeks ago, I signed up for a webinar from the DMA. As is my normal process I used a tagged address. I don’t remember any notification that I would be signing up for mail, and I generally do look for those kinds of things. I also know a lot of webinars are used to drive sales processes and I prefer not to waste sales time if I’m not actually looking to purchase.
In recent weeks I have gotten an ongoing stream of marketing messages from the DMA. I’ve tried to opt-out, but the DMA don’t actually want me to opt-out. Each marketing message is a different type of message from a different list. Each list must be opted out of individually.
First it was Conferences, then it was Education, then it was Awards, then Events. I’m trying to figure out what’s next and how many more times the DMA is going to get to spam me before I just turn that address into a spam trap.
And before you tell me that I can’t make an address a spam trap, think about that a little bit. I never opted this mail in to receive anything but the webinar confirmation. I’ve dutifully opted out each and every time the DMA has mailed me. I’ve even tried to opt-out of all mail. Unfortunately, the DMA has placed the “opt-out of all mail” behind a registration wall, one I cannot get to as I do not have (or want) a DMA account.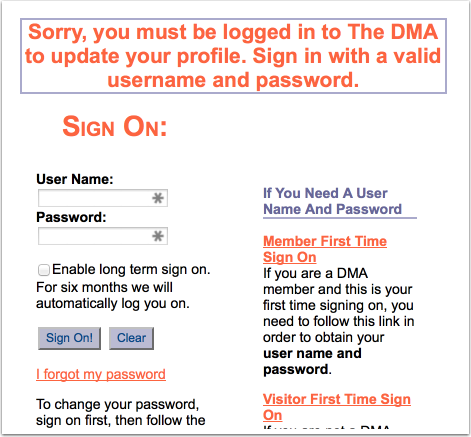
The DMA is sending me mail I did not request and do not want. They have made it impossible for me to determine how much mail I will get. They have made it difficult for me to opt-out of all their mail.
This is an example of bad email marketing. I’m sure that the DMA will tell me this is all permission based email. I disagree. This is an example of the DMA taking permission. This is not an example of a sender asking for permission. I didn’t give permission to be added to all these DMA lists, and I have no way to actually revoke the permission that they took from me.
I signed up for a second webinar with this email address, one related to CASL. The irony is that the DMA’s behavior here is a violation of a number of points of CASL. First, there was no clear opt-in notice on the website. Second, CASL requires parity between opt-in and opt-out. If I opt-in once then I should be able to opt-out once. CASL puts an end to this opt-in once, opt-out dozens of times process.
I wish I could say I was disappointed in the DMA. But I’m barely surprised. Their track record is poor and they have typically fallen on the side of “I have consent until you force me to acknowledge that I don’t.” In this case, the DMA is demonstrating that quite clearly. They will keep spamming and spamming and spamming. I have no doubt were I to actually register an account, they would continue to spam me with “account notifications” that I was unable to opt-out of because they are transactional, membership messages.
Happy 4th of July
- laura
- Jul 4, 2014
We’re off to eat hot dogs and ice cream and watch fireworks with KarlTheFog.
Have you met KarlTheFog? We visited him earlier this month and I took some pictures.
Have fun storming the CASL!
- steve
- Jul 3, 2014
I’ve given Humble Bundle my (tagged) email address a bunch of times – as part of purchases, as my username on their website, to download games and books I’ve bought.
And, naturally, they’ve sent me newsletters announcing when they have new sales. Did I check a checkbox or uncheck a checkbox? I don’t remember, and don’t really care. It’s a company I have a real relationship with and have purchased from, they’re sending content I want to see, and I trust them not to misuse my address and to honour an unsubscription request.
So … probably opt-in, and I’m fairly sure they’ve confirmed that it’s my email address. But did they explicitly tell me they’d use my email address for a newsletter? I and my email archive don’t remember that far back, and it’s quite possible that Humble Bundle’s current staff and records don’t either.
In todays newsletter, right above their talking about their summer sales, they had this:
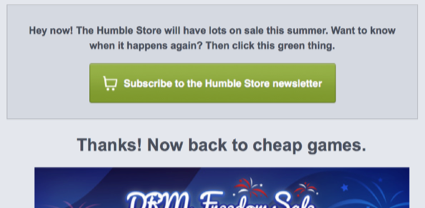
They’re confirming that I want to keep getting newsletters, and stressing why I want to keep getting them. Their database probably dates back to the iron age, or at least 2010, and my clicking on the big, friendly green button both lets them know that I’m an engaged subscriber and lets them record in their database that “Yes! This subscriber has explicitly said they want our newsletters!”.
Gradually adding that information to their subscriber database will let them better make decisions in the future about what content to send, how often, whether to try and reengage with a subset of their subscribers.
Oh, and there’s CASL, of course.
If you or your recipients have a Canadian presence you have a little less than eighteen months to make sure you have documented, explicit consent from any recipients for whom you only have implicit (e.g. business relationship) consent or for whom you’ve lost the original records.
June 2014: The month in email
- laura
- Jul 2, 2014
Each month, we like to focus on a core email feature or function and present an overview for people looking to learn more. This month, we addressed authentication with SPF.
We also talked about feedback mechanisms, and the importance for senders to participate in FBL processes.
In our ongoing discussions about spam filters, we took a look at the state of our own inboxes and lamented the challenge spam we get from Spamarrest. We also pointed out a post from Cloudmark where they reiterate much of what we’ve been saying about filters: there’s no secret sauce, just a continuing series of efforts to make sure recipients get only the mail they want and expect to receive. We also looked at a grey area in the realm of wanted and expected mail: role accounts (such as “marketing@companyname.com”) and how ESPs handle them.
As always, getting into the Gmail inbox is a big priority for our clients and other senders. We talked a bit about this here, and a bit more about the ever-changing world of filters here.
On the subject of list management, we wrote about the state of affiliate mailers and the heightened delivery challenges they face getting in the inbox. We got our usual quota of spam, and a call from a marketer who had purchased our names on a list. You can imagine how effective that was for them.
And in a not-at-all-surprising development, spammers have started to employ DMARC workarounds. We highlighted some of the Yahoo-specific issues in a post that raises more questions.
We also saw some things we quite liked in June. In the Best Practices Hall of Fame, we gave props to this privacy policy change notification and to our bank’s ATM receipts.
We also reviewed some interesting new and updated technology in the commercial MTA space, and were happy to share those findings.
Happy Canada Day, CASL now in effect
- laura
- Jul 2, 2014
It’s Canada Day, and this year it has special connotations for email senders who are in Canada or sending to Canadian residents.
CASL is now in effect. For in depth guidance, go visit Matt Vernhout’s excellent series on CASL. But for those of you who just want the Cliff notes here’s the high points
If you are in Canada or you are sending to residents in Canada:
Incorrect rejection messages
- laura
- Jun 27, 2014
At least one ESP and Spamhaus are currently investigating bounce messages at a couple ISPs incorrectly pointing to Spamhaus as the reason for the block. The bounce messages are taking the form:
Read MoreSpam disclaimer of the day
- laura
- Jun 26, 2014
Things are extremely busy here so blogging is not getting quite the attention it should. I hope to return to more extensive posts soon. Meanwhile, you’ll have to put up with short posts.
Today is a disclaimer I received in a spam. This is one of my addresses that has, somehow, ended up on UK-specific lists.
Ever changing filtering
- laura
- Jun 26, 2014
One of the ongoing challenges sending email, and managing a high volume outbound mail server is dealing with the ongoing changes in filtering. Filters are not static, nor can they be. As ISPs and filtering companies identify new ways to separate out wanted email from unwanted email, spammers find new ways to make their mail look more like wanted mail.
This is one reason traps are useful to filtering companies. With traps there is no discussion about whether or not the mail was requested. No one with any connection to the email address opted in to receive mail. The mail was never requested. While it is possible for trap addresses to get on any list monitoring mail to spam traps is a way to monitor which senders don’t have good practices.
New filtering techniques are always evolving. I mentioned yesterday that Gmail was making filtering changes, and that this was causing a lot of delivery issues for senders. The other major challenge for Gmail is the personalized delivery they are doing. It’s harder and harder for senders to monitor their inbox delivery because almost every inbox is different at Gmail. I’ve seen different delivery in some of my own mailboxes at Gmail.
All of this makes email delivery an ongoing challenge.
Outlook 365 having a bad day
- laura
- Jun 24, 2014
I’ve seen scattered reports today that some mail to the Outlook 365 servers is failing. This has been confirmed by ZDNet. Only folks with a Office 365 account can log in and see the status messages, but there are some folks on the mailop list posting updates from the website.
Attempts to mail to affected domains results in this response:
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Backus-Naur Form
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcc
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- BIMI
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cabbage
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- CFWS
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- DMARC
- DNS
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Strategy
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- GDPR
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- IPv4
- IPv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Message-ID
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Needs Work
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Re-Engagement
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Replay
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- RFC
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- SPF
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Undisclosed Recipients
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb