Don't send customer-generated content
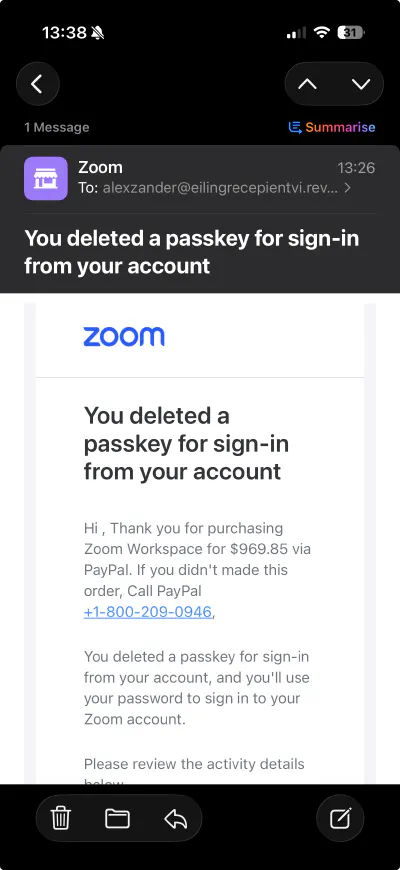
I just got this email:
SPF is valid. It passes DKIM for zoom.us.
It has enforcing (p=reject) DMARC for zoom.us, which passes.
My mail setup doesn’t display BIMI, but there’s a valid BIMI record for zoom.us and a mailbox provider might display the nice Zoom logo and checkmark next to it. (They also might not, given the number of technical red flags under the covers, but I wouldn’t blame them if they did.)
Zoom are vouching for the legitimacy of this email, in every way that matters.
It is, of course, a phishing email.
So why are Zoom saying it’s legitimate? As usual, it’s a DKIM replay.
The bad actor created a throwaway domain, eilingrecepientvi.review, and set up an email account there at an often abused german hosting provider. Then he signed up for a - free, presumably - Zoom account using that email address.
He told Zoom that his name was “, Thank you for purchasing Zoom Workspace for $969.85 via PayPal. If you didn't made this order, Call PayPal +1-800-209-0946,”.
This didn’t raise any flags at Zoom.
He created a throwaway account at Microsoft - never trust any email with any mention of onmicrosoft.com in it, it’s all scams - and set it up to forward to his list of potential victims. And told his oft-abused hosting provider to forward mail there.
Then he made some changes to his Zoom account to trigger a DKIM-signed email to be sent to his throwaway email address, including his entire phishing message in the “Dear
Because it was sent via Microsoft, with an onmicrosoft.com return-path, SPF passes. Because the content of the body of the email is unchanged from when Zoom originally sent it, the DKIM signature Zoom applied to it still passes.
So it’s fully authenticated when the victim receives it. The only recipient visible sign that it’s not legitimate is that their email address isn’t in the To: field.
Who’s at fault here?
The domain is obviously suspicious, but probably no more so than anything else in the .review TLD. The - perfectly reputable - domain registrar can’t reasonably do anything differently. I’ve used them in the past; they’re fine.
The low budget, oft-abused hosting provider who provide the infrastructure for the throwaway email address are just doing what they do - providing inexpensive self-signup hosting. Other than responding to abuse reports after the fact there’s not much they can do. They’re just like a bunch of hosting providers I use quite happily.
The US VOIP provider that’s renting out the 800 number that’s being used to collect victims, presumably to social engineer their paypal, or banking or credit card details is, again, just providing reasonably priced self-signup VOIP service. I’ve used them in the past; they’re fine.
Microsoft, eh, they know that their eval / deployment setup using onmicrosoft.com is a bit of an abuse magnet but they are looking at how to mitigate that.
Zoom, though, made a classic blunder, only slightly less well-known than “Never go in against a Sicilian, when death is on the line!”. They accepted arbitrary user-generated content for use in an email they sent.
Yes, even the user’s name is user-generated content.
On the modern Internet this is just asking to have your reputation abused for phishing.
This isn’t just a Zoom mistake. We see exactly the same blunder from large organizations with sensitive reputations. Paypal1. Intuit. Lots of others.
Any time you’re accepting content from customers, especially customers who are on free accounts or free trials, consider how your use of it can be abused.
Limit the length. Don’t allow HTML. Check for homoglyphs. If it’s not a telephone number field, don’t allow ‘phone numbers. If it’s not an email address field, don’t allow email addresses. Flag any attempt to insert a hostname (that a mail client may make clickable). And really, nobody has the word “paypal” in their name.
You don’t have to block a customer from entering this sort of thing - though it’s probably a sign that they’re not a legitimate customer - you can just prevent it’s use in email. Fall back to the “we have no data” placeholder instead.
“Dear Generic Customer,” is much better than “Dear Thank you for purchasing Zoom Workspace for $969.85 via PayPal…”.
Consider how it’s displayed in the mail you send. If you include something like a customer provided memo in a callout box at the top of your email then it will look like that is what the email is about.
If a bad actor can’t inject their content into mail you send then there’s very little incentive to target you for DKIM replay.
PayPal say they’ve mitigated one of the channels being used for this, as of last month. The rate of PayPal phishes I’m seeing through other companies supports that. ↩︎