Stop using Entrust for your BIMI Certificates
In July I talked about how Entrust was mistrusted by, well, pretty much everyone due to a years long series of security and trust violations.
At that time Google had removed Entrust from the certificate roots trusted by the Chrome browser – the nuclear option, showing that Entrust is really, really not seen as trustworthy. They hadn’t – yet – taken any action regarding BIMI VMCs issued by Entrust.
Apple
But Apple have recently stated they’re taking similar action with their set of trusted roots, such that any certificate issued by Entrust after November 15th will be treated as untrusted.
And that includes BIMI certificates:
The following Root CA Certificate is impacted for Brand Indicator for Message Identification (BIMI):
Certificate Name SHA-256 Fingerprint
Entrust Verified Mark Root Certification Authority – VMCR1 – 7831D95A47D42508CD5C9E6264F9096BAC19F04EB9B7C8BDD35FFFC71C18961
Entrust
This is what Entrust have to say about it:
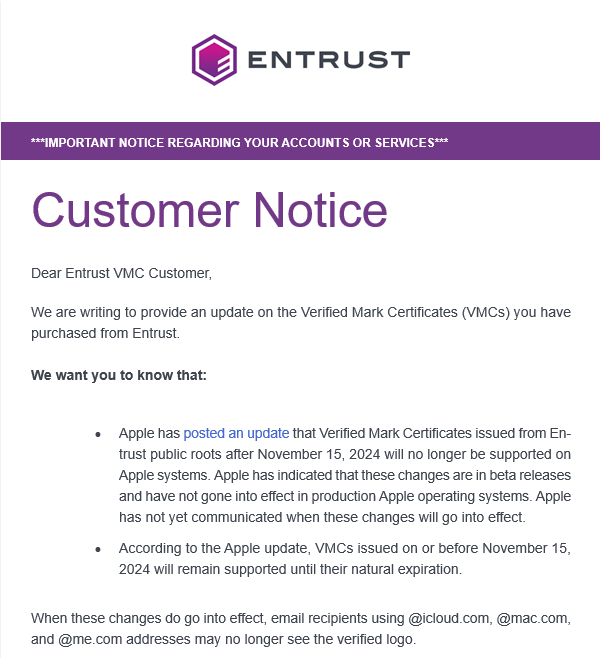
What now?
If you’re using DigiCert for your BIMI certificates there’s nothing to worry about.
If you’re using Entrust, and your certificate was issued before November 15th 2024 then it will continue working at Apple for now – but when it’s renewed it will stop working. You should make sure you have a path in place to migrate to a certificate issued by DigiCert before your current certificate expires. If it were me, I’d start that migration as soon as I was back in work in January.
If you’re using Entrust and your certificate was issued after November 15th 2024 then it is not considered valid by Apple, and will stop working as systems are updated. You should migrate to DigiCert as soon as possible (and probably try and claw back any payment made to Entrust).
What CA am I using for BIMI?
If you have a linux, macOS or wsl shell handy you can check like this:
% dig +short default._bimi.paypal.com TXT
"v=BIMI1; l=https://www.paypalobjects.com/marketing/web/logos/paypal.svg;
a=https://www.paypalobjects.com/marketing/web/logos/paypal_com.pem"Code language: PHP (php)(“default” is the default BIMI selector. You need to see a BIMI using email to know for sure which selector is being used, but “default” is a good guess as it’s, well, the default.)
Check the result from dig and copy the URL from the a= field, then use curl, openssl1 and grep to find the issuer. It’s a one-line command, ignore the line breaks.
curl -s https://www.paypalobjects.com/marketing/web/logos/paypal_com.pem
| openssl x509 -text -noout | head
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
04:4b:c5:28:85:8a:de:27:ba:f4:6a:01:1f:78:37:ba
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, O=DigiCert, Inc., CN=DigiCert Verified Mark RSA4096 SHA256 2021 CA1
Validity
Not Before: Jun 12 00:00:00 2024 GMT
Not After : Jul 3 23:59:59 2025 GMTCode language: JavaScript (javascript)You can see that PayPal is using a BIMI certificate that was issued by DigiCert on June 12th, 2024.
(You can also send an email to https://aboutmy.email/ and see details about the BIMI certificate in use on the BIMI tab).
- If you’re on a mac you won’t have the openssl tool by default, but it’s available from HomeBrew, amongst other places. Grab a copy, it’s often useful. ↩︎