Why is DMARC failing?
Multiple times over the last few weeks folks have posted a screenshot of Google Postmaster tools showing some percentage of mail failing DMARC. They then ask why DMARC is failing. Thanks to how DMARC was designed, they don’t need to ask anyone this, they have all the data they need to work this out themselves.
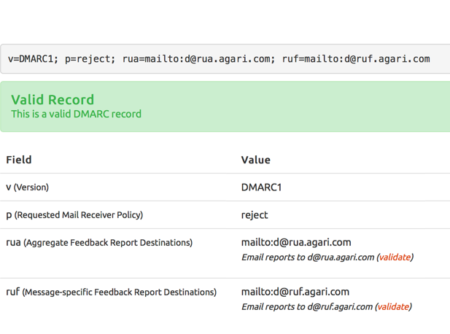
The DMARC protocol contains a way to request reports when DMARC authentication fails. There are even two different kinds of reports: aggregate and per-message reports.
The major mailbox providers send aggregate DMARC reports. These reports show a summary of messages received using the domain’s from address and report all authentication failures for those messages. According to the specification aggregate reports should contain the following information:
- The DMARC policy discovered and applied, if any
- The selected message disposition
- The identifier evaluated by SPF and the SPF result, if any
- The identifier evaluated by DKIM and the DKIM result, if any
- For both DKIM and SPF, an indication of whether the identifier was in alignment
- Data for each Domain Owner’s subdomain separately from mail from the sender’s Organizational Domain, even if there is no explicit subdomain policy
- Sending and receiving domains
- The policy requested by the Domain Owner and the policy actually applied (if different)
- The number of successful authentications
- The counts of messages based on all messages received, even if their delivery is ultimately blocked by other filtering agents
Reports come in XML format, which is very difficult to read without some processing. But, anyone who is publishing DMARC records should have some way to read aggregate reports at a minimum. These are, to my mind, the actual useful piece of the protocol.
The other type of reports are per-message or forensic reports. These reports contain copies of the whole message. Last I heard there weren’t many providers sending forensic reports, which is fine because that has the ability to melt down servers from the sheer volume of mail.
Next time you see GPT with DMARC failures, go check your DMARC reports. That will tell you what’s failing and from where. If there’s a problem you’ll be able to tell and address it. No need to go ask anyone outside your organization or DMARC processor for help.
