DMARC doesn’t fix phishing
Over the last few weeks I’ve had a lot of discussions with folks about DMARC and the very slow adoption. A big upsurge and multiple Facebook discussions were triggered by the ZDNet article DMARCs abysmal adoption explains why email spoofing is still a thing.
There are a lot of reasons DMARC’s adoption has been slow, and I’m working on a more comprehensive discussion. But one of the absolute biggest reasons is that it doesn’t actually fix phishing.
One of the first adopters of DMARC is PayPal. But being an early adopter and publishing a p=reject for years and years has not actually stopped the bad guys from sending PayPal phishes. Here’s an example of one I received recently.
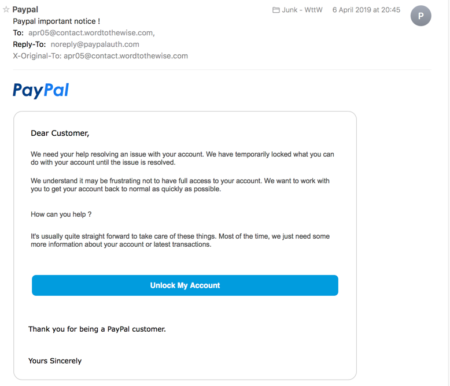
The message clearly shows it’s from PayPal. The sending domain is authenticated with SPF. The SPF domain and the 5322.from domain align. The message is DMARC authenticated.
No, the domain in the From: address isn’t @paypal.com, but that doesn’t matter because a huge number of mail clients, including Gmail, Hotmail, Apple Mail, and Outlook hide the actual email address from the user. All it displays is the so-called friendly from.
The people who think DMARC should be a requirement for email will tell you that this is not the problem space DMARC is supposed to fix. That DMARC is solely intended to fix direct domain spoofing. This is true, DMARC is not intended to fix this type of phishing.
I actually put a lot of blame at the feet of mail client developers. I don’t know who thought it was a good idea to hide the 5322.from address from the user, but they were wrong. To my mind it’s a bad user experience and makes recipients more vulnerable to falling for phishing schemes.
I understand that DMARC isn’t intended to fix this type of phishing. But the fact that it doesn’t fix this type of phishing makes it a whole lot less useful as an anti-phishing product. The tiny scope of DMARC and the expense of implementing it is one of the primary reasons it’s not more widely deployed.
The interesting bit, though, is even without widespread deployment, phishers have changed their attacks. We can declare DMARC a success at stopping direct domain phishing, even though there’s a less than 25% adoption rate. The phishers have moved on. Now, maybe we should look at other ways to address the phishing problem, one that encompasses the majority of attack vectors, rather than a very narrow one.