The Blighty Flag
- laura
- November 3, 2017
- Best practices
Back in the dark ages (the late ’90s) most people used dialup to connect to the internet. Those people who had broadband could run all sorts of services off them, including websites and mail servers and such. We had a cable modem for a while handling mail for blighty.com.
At that time blighty.com had an actual website. This site hosted some of the very first online tools for fighting abuse and tracking spam. At the same time, both of us were fairly active on USENET and in other anti-spam fora. This meant there were more than a few spammers who went out of their way to make our lives difficult. Sometimes by filing false complaints, other times by actually causing problems through the website.
At one point, they managed to get a complaint to our cable provider and we were shut off. Steve contacted their postmaster, someone we knew and who knew us, who realized the complaint was bogus and got us turned back on. Postmaster also said he was flagging our account with “the blighty flag” that meant he had to review the account before it would be turned off in the future.
I keep imagining the blighty flag looking like this in somebody’s database.
That is to say, sometimes folks disable accounts they really shouldn’t be disabling. Say, for instance: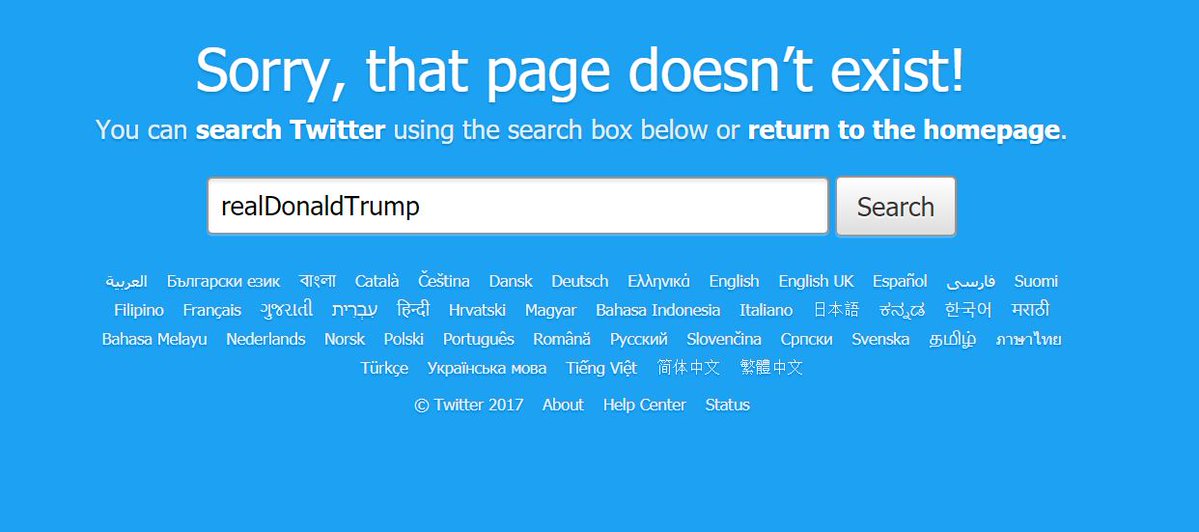
This was an accident by a twitter employee, according to a post by @TwitterGov
Earlier today @realdonaldtrump’s account was inadvertently deactivated due to human error by a Twitter employee. The account was down for 11 minutes, and has since been restored. We are continuing to investigate and are taking steps to prevent this from happening again.
— TwitterGov (@TwitterGov) November 3, 2017
Twitter needs a blighty flag.

