Reaching targets, the wrong way
I’ve been increasingly annoyed by these drip automation campaigns. You know the ones I mean. Senders use some software to find some flimsy pretext to send a mail. Then there emails drop every few days. Sometimes this cycle goes on for months. Most of these messages violate CAN SPAM. It’s annoying. It’s illegal. It is spam.
I can even opt out of most of these messages, they don’t offer that ability.
Spammers Gonna Spam
I have so many examples of these emails. They’re all the same, really. They start out with a statement someone is reading my website. Then they mention they have an article that they or their customers wrote. This article is, of course, perfect for my site and the article.
Well that’s the theory anyway. They tend to miss the mark pretty significantly.
There was this one example where the company found a post linking to a newspaper article.
Hi there,I was just browsing Word To The Wise and saw you were interested in travel from this post (https://wordtothewise.com/2011/01/fines-for-not-honoring-unsubscribes/). So I thought you might also be interested in linking to a resource we put together on how travelling can improve your health.Here is a link for your review:
Hey Lauren –
I hope everything is going well on your end 🙂
I just finished going through your article here: https://wordtothewise.com/2015/04/a-series-of-tubes/. Thanks for the resource!
My colleague Lavanya put together a pretty comprehensive piece on the net neutrality just last week.There is a lot of info out there about net neutrality, and it’s sort of a hot topic at the moment. Our guide was designed to cut through the noise a bit.
The article is here: [link removed]Would you consider linking to it in the post of yours I mentioned above? I saw you linked to en.wikipedia.org in there, so I figured I’d see if you’d link to mine as well. Perhaps your visitors find it helpful, but hey, it’s up to you.
Thanks,- Eric
P.S. I respect the relationship you have with your readers, I wouldn’t ask you to link to anything I didn’t think was an excellent resource for your site.
B2B spam is still spam
I was recently contacted by one of the software companies that provides infrastructure for these types of emails. Surprisingly, they are having a difficult time getting their mail delivered. It seems no one wants their mail. The thing is, I can’t help them. No one can help them. They’re sending mostly unwanted mail. I’m sure even the bloggers who make their money from blogging hate these kinds of messages.
This was someone building software that is causing significant amount of annoyance. I get the messages this software company, and their competitors, are facilitating. I am not going to help their spam get through to people who don’t want it.
During the call, they did name some of their competitors and I fell down the rabbit hole of B2B spamware. The vendors go through all sorts of contortions to convince their users this isn’t spam. Many of the phrases used on the websites were the same I heard on the phone. It’s one-to-one mail. It’s targeted. It’s focused on the recipient. It’s important.
Guess what? I’m a frequent recipient of that kind of mail. I know the mail isn’t targeted and it’s not focused on the recipient. The two examples above show that clearly. One of them couldn’t even get my name right! Both of them missed the context of the links and posts. None of this has to do with me or my readers, other than an example of what not to do.
CAN SPAM applies
The term “commercial electronic mail message” means any electronic mail message the primary purpose of which is the commercial advertisement or promotion of a commercial product or service (including content on an Internet website operated for a commercial purpose).
Unwanted mail doesn’t reach the inbox.
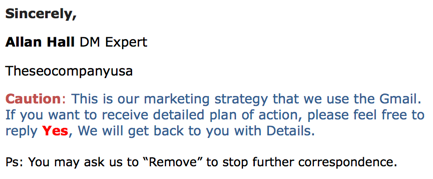
Last week’s phone call demonstrated I am not alone in hating this mail. The software company contacted me for help because they can’t get to the inbox. It seems no one wants their mail. Due to blocking problems many of the senders resort to tactics used by spammers. They use different domains for their unsolicited mail. Sometimes they’re analog or cousin domains, like a .co for the unsolicited messages and a .com domain for their response emails. In other cases, they use Office365 or Google apps or Gmail for their outbound mail stream. Most places won’t block @gmail.com, so it’s a fairly safe to use gmail addresses.
Permission is key to delivery
Marketing programs that rely on spammer tactics are doomed to failure long term. Mail sent without permission does not work, even in the B2B space. Companies relying on unsolicited email discover it’s not that simple. Spam filters block unsolicited email. That’s their job, it’s what they’re designed to do. The way they detect unsolicited varies, but filters target unsolicited email.
There are large companies, many of them clients of mine, who do get caught in filters, usually because some of their mail is unsolicited. This isn’t intentional. Their overall program is sending mail to people who have asked for it and want it. Permission is a central piece of the email strategy. But, particularly as programs age, we find grotty corners where permission is a little iffy. These are small parts of their database, but they can cause significant problems.
Good email marketers know that permission is key. They invest time, energy and resources into getting permission and maintaining data. They think long term. They know recipients don’t want spam and that any gains from spamming are fleeting.