This showed up in my mailbox earlier today:
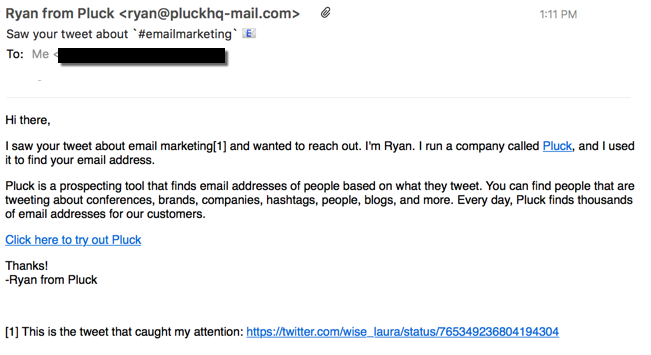
The tweet in question
From Crunchbase: “Pluck is an email prospecting tool that gives you the email addresses of the people tweeting about subjects related to your business.”
Prospecting: another name for spamming. Look, I know that you want to sell you’re newest, greatest product to the world. But just because I tweet something with a # that you think is relevant to your product doesn’t mean that I want to get your spam. I also know it’s hard to get attention and find prospects; I’m a small business owner, too and I need to market my own services. But spamming isn’t a good idea. Ever.
There’s been a significant increase in this kind of spam “to help your business” lately. It’s a rare day I don’t get something from some company I’ve never heard of trying to sell me their newest product. It might be something if they tried a contact or two and then went away. But they’ll send mail for weeks or months without getting an answer. Look, silence IS an answer and it means you need to go away and leave your prospects alone.
Unfortunately, there are services out there that sell a product that let you “automatically follow up” with your prospects. Pluck up there uses one of them, as that’s who’s handling all the links in the message. In fact, if you go to the bare domain (qcml.io) they talk a good anti-spam game. “Die, spammers, die.” I reported the message to them. I’m not expecting them to actually do anything, and I’m not expecting a response.
It’s just spam under another name. There’s no pretense that it’s anything else. Even if it’s sent in a way that makes it look like a real person typed the message, like QuickMail offers. “All emails will come straight out of your personal inbox as though you typed them yourself.” As if you typed them yourself.
The worst part is there’s no real way to stop the mail. I can’t unsubscribe. The companies selling the software don’t provide any guidance to their customers about what the law requires. Take the message from Pluck that started the post. It violates CAN SPAM in multiple ways. Moreover, the address they used is not publicly associated with my twitter handle, which means they’re doing some harvesting somewhere. That means treble penalties under CAN SPAM.
I could reply and ask them to stop mailing me. I’ve done that a couple times with a message that says, “Please don’t email me any more.” I’ve got to tell you, some people get really mad when you ask them not to email you. Some just say yes, but others are really offended that you asked them to stop and get abusive. It’s gotten to the point where I don’t ask any more because of that one person who decides to harass, threaten and scream at me. Sure, it’s maybe 1 in 5, but I don’t have the time or energy to figure out who is going to be receptive and who isn’t. I don’t have time for that. No one has time for that.
I’m expecting that filters are going to catch up eventually and these types of mail will be easier to filter out. Until then, though, small business owners like myself are stuck in a place where we have to deal with spam distracting us from our business. At least I get blog content out of it.
Read More

